Operations | Monitoring | ITSM | DevOps | Cloud
November 2022
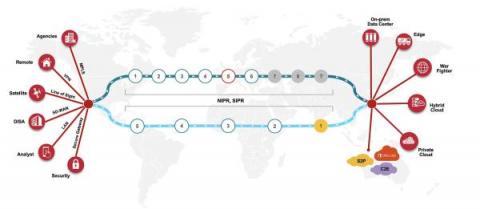
Broadcom Software Debuts the Experience-Driven NOC at DoDIIS 2022
Command, control, and communications (C3) systems are fundamental to all military operations, and the network is the backbone to keeping the warfighter up to date and out of harm's way. The right network modernization strategies will enable the latest C3 capabilities to provide real-time situation awareness and decision support for today’s military operations.
Kentik Kube: Container Network Performance Monitoring
MSSP Maturity Levels and Building Out Your Offering - Empower 2022 Panel
Close the Cloud Monitoring Gap with Network Observability
To fully capitalize on the promises of digital transformation, IT leaders have come to recognize that a mix of cloud and data center infrastructure provides several business advantages, including increased agility, cost efficiencies, global availability, and, ultimately, better customer experiences.
WireGuard vs OpenVPN: Which VPN Protocol Is Better?
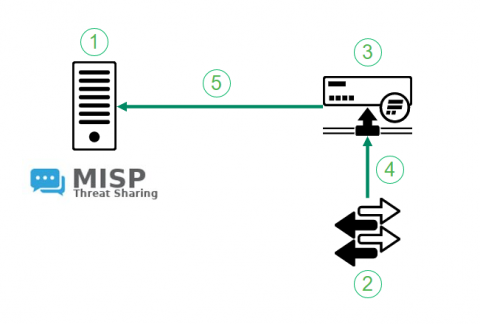
Flowmon Anomaly Detection & MISP
Back in 2021 we have introduced the integration between MISP, a community threat intelligence sharing platform and Flowmon ADS. The integration turns indicators of compromise shared through MISP to actionable intelligence. Flowmon ADS will automatically pick up on latest indicators of compromise using MISP API and leverage those indicators of compromise to detect adversary activities in the target network. The integration is available in Flowmon ADS 11.2 and newer versions.
Multi-cloud trends in the healthcare sector
4 Most Common Website Security Threats (2023) + Solutions
For infrastructure administrators tasked with ensuring the reliable operation of their applications, the thought of a lurking cyberattack can be one to lose sleep over. An attack on your system and the services you provide could render your applications unresponsive, resulting in a security breach, or loss of data.
3 Most Common SD-WAN Issues
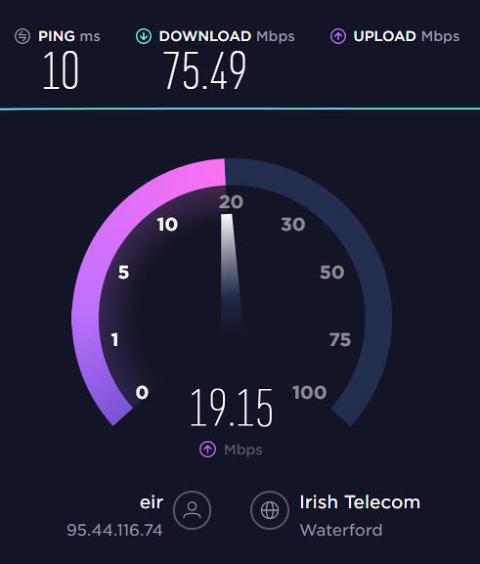
How to monitor Internet quality and ISP performance with Netdata
Find out how to monitor your Internet speed and quality and how well your ISP is performing.
Crous Paris Mitigates Network Outages Before Students Notice with Progress WhatsUp Gold
How to Automate and Orchestrate Your Network Effectively
We explain how to make the most of automation, orchestration, and Infrastructure as Code tools for your highest performing network yet.
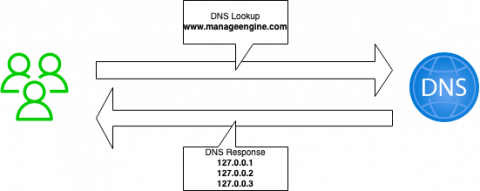
How network admins benefit from DNS failover
Downtime is a nightmare, and every network or app administrator wants to avoid it in any way they can. The longer the downtime, the greater the potential for a loss of revenue and a damaged reputation for the organization.
Cybercrime Trends and the Economy
What is Network Flow Monitoring, and Why You Shouldn't Live Without It
Old network salts likely know all about network flows and the value of network flow monitoring. As former News Editor for Network World and Editor in Chief of Network Computing, network flows are part of my old stomping grounds. In fact, I remember when Cisco invented NetFlow in the late 1990’s to collect traffic data from its routers and switches so it could be analyzed by network pros.
Building AppStack Dashboards
What is Network Performance Monitoring?
Hidden Costs of Cloud Networking: Optimizing for the Cloud - Part 3
I used the first two parts of this series to lay out my case for how and why cloud-based networks can effectively “Trojan horse” costs into your networking spend and highlighted some real-world instances I’ve come across in my career. In the third and final installment of this series, I want to focus on ways you can optimize your personnel and cloud infrastructures to prevent or offset some of these novel costs.
Optimize Your NOC with DX NetOps and Automic Automation
Learn how Automic can help NetOps speed up triage, reduce MTTR, and alleviate the load on your NOC Today’s network team is committed to advancing the speed of triage and resolution. This can be a titanic task in modern networks, which are fueled by SDN and becoming more agile and dynamic than ever. These new networks have introduced traffic, congestion, and outages on a greater scale.
Sunrex Technology Removes Network Security Bottlenecks in Information Security with Progress Flowmon
Botswana Telecommunications Corporation Limited (BTC) partners with Infovista for optimization of its mobile network
8 Wi-Fi Mistakes Everyone Makes
HAProxyConf 2022 Recap
Earlier this month, I packed my bag and grabbed my lanyard to attend HAProxyConf in the beautiful city of Paris. I was far from alone: nearly 200 customers, colleagues, and community enthusiasts had the same idea. We overcame jetlag, stagefright, and introverted personality types for the joy of meeting and learning from some of the brightest minds in the industry. From load balancing to cybersecurity to endless cups of strong coffee: this is HAProxyConf 2022!
Intelligent Network Monitoring and Visibility - and Why It Matters
The Next Evolution of Hybrid Cloud Network Monitoring
How Green Is Your Network?
As the tech industry goes green, how does your network stack up – and how can you make it greener?
5 Web Security Tips For Small Businesses
BGP Monitoring with Catchpoint: Finding and Fixing BGP Issues - FAST
BGP is effectively the postal service of the Internet. Without BGP, traffic doesn't move. So, when there's a configuration issue, or worse, malicious activity – the repercussions can be huge. That's why constant monitoring of BGP traffic is crucial. In this ten-minute video, Solutions Engineer Zach Henderson explains why BGP issues can damage your bottom line and then shows how to quickly detect, analyze and resolve them with Catchpoint's market-leading BGP Monitoring solution.
How the telco industry is embracing blockchain innovation
Shorten Recovery from Cyberattack with Cove's Standby Image
What is Network Mapping and What is it Good For?
Try to explain your network topology to a stranger in a bar and you’ll get a blank stare—the same look your CEO would give. Show that CEO a map, report or even your network monitoring dashboard, and recognition will creep across their face.
SD-WAN Troubleshooting: How to Troubleshoot SD-WAN Networks
Webinar Snippet: How to Troubleshoot SD-WAN Networks | Obkio
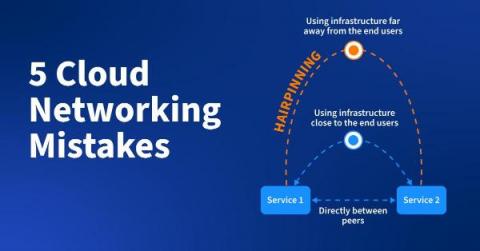
Avoid These Five Cloud Networking Deployment Mistakes
When transitioning from physical infrastructure to the cloud, it’s easy to think that your networks will instantly be faster, more reliable, and produce windfalls of cost savings overnight. Unfortunately, this wishful line of thinking fails to account for some of the complexities of cloud networking and is one of the biggest drivers of the cloud deployment mistakes we see.
What is SD-WAN technology, and how does it work?
Research on Optical Module in FPGA Optical Fiber Transmission Circuit
Being Secure When Moving to the Cloud - N-able Chief Security Officer David MacKinnon - Empower 2022
Why Hybrid Network Monitoring is Key for Retailers This Holiday Season
The main street in my town is mostly lined with mom-and-pop shops, and I love to support these businesses. Large online retailers keep making it harder for these stores to compete, so I think it’s important to keep doing business with them when I can. Lately, it’s been interesting to see that these mom-and-pop shops increasingly have something in common with the largest online retailers: They’re reliant on the internet to deliver their goods and services to consumers.
Suppressing Dissent: The Rise of the Internet Curfew
In the evening on September 30, people across Cuba found their internet service cut. The residents of this Caribbean nation had begun protesting their government’s tepid response to Hurricane Ian which had wrought destruction a week earlier. Internet service returned to normal the following morning, but this outage wasn’t caused by storm-related damage. This blackout was a deliberate act, a fact confirmed when service dropped out for the same period of time the following day.
Internet 101: A Complete Guide and Explanation of the Internet
N-able Accelerates Global Support for MSPs and IT Resellers Through Expansion of Dedicated Distributor Network
Five Issues Your NetOps Team Will Face in the Cloud
For organizations of all types and sizes, networks are more than just a line item on a departmental budget. Modern digital enterprises understand that long-term competitiveness depends on maximizing their IT assets to create exceptional user experiences.
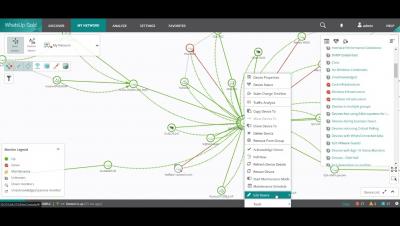
WhatsUp Gold Demo
How NaaS and SDCI Can Lower Your Cloud Spend
Cloud costs can pile up quickly, and often behind the scenes. We explain how software-defined cloud interconnect (SDCI) can help your business rein in a swelling budget.
Playing to Win in the Cloud - Mike Adler Empower 2022 Keynote
Everything You Need to Know About Synthetic Testing
Part two of a three-part guide to assuring performance and availability of critical cloud services across public and hybrid clouds and the internet Monitoring your user traffic is critical for knowing the quality of the digital experience you are delivering, but what about the performance of new cloud or container deployments, expected new users in a new region, or new web pages or applications that don’t have established traffic? This is where synthetic testing can be invaluable.
Using Kentik Synthetics for Your Cloud Monitoring Needs
The final post of a three-part guide to assuring performance and availability of critical cloud services across public and hybrid clouds and the internet Kentik Synthetics adds integrated, autonomous, pervasive performance test telemetry to our market-leading network traffic analytics and observability platform, the Kentik Network Observability Platform. For modern clouds, proactive synthetic monitoring can no longer be delivered as a standalone tool.
A Guide to Cloud Monitoring Through Synthetic Testing
A three-part guide to assuring performance and availability of critical cloud services across public and hybrid clouds and the internet.
5 Important Operations Issues to Consider When Working With an International Team
SolarWinds Review: SolarWinds vs. MetricFire
SolarWinds is a network and application monitoring solution, but primarily a network monitoring solution. Founded in 1999, the company has built an online community of 150,000 registered users. However, monitoring has come a long way since the early 2000s. How does SolarWinds stack up against MetricFire in terms of features and pricing? In this article, we break down the comparison into easily digestible, unbiased information to help you make an informed decision.
Do VPNs Really Keep Your Browsing Data Private?
Kentik takes network observability to KubeCon 2022
If you’re an engineer trying to fix real problems with your apps, looking at just one small part of the picture isn’t going to cut it. This is why Kentik is so focused on helping you understand what’s going on beyond single k8s instances, and it’s a big part of what network observability is all about. This was Kentik’s message at Kubecon 2022, which was a memorable event for us.
A tool is only as good as the people behind it
Solving for cloud/multi-cloud network complexity
Using the REST API Monitoring Support in WhatsUp Gold
Network Monitoring for Dummies
HAProxy Introduces General Availability of HAProxy Fusion Control Plane
MSPs are living in the "Platinum Era". So what?
Network Documentation Best Practices: What to Create & Why
Half of IT pros say increased complexity is the number one issue facing their organisation
Protecting Your VoIP Infrastructure From DDoS Attacks
Distributed denial of service (DDoS) attacks are an ongoing issue for communications service providers, putting critical systems at risk, undercutting service level agreements, and bringing unwanted headlines. In the first half of 2022 6 million of these attacks were reported. Some metrics of DDoS attacks in 1H2022 compared to 2H2021.
AWS, Azure, and Google Cloud: The Big Three Compared
These three top cloud providers are used daily by millions of users across the world – but what sets them apart? We take a magnifying glass to the features that matter.
Scaling Up, One Network Bottleneck at a Time
Are you a network observability champion?
At Kentik, we pride ourselves as innovators and thought-leaders for network observability. “Kentik is network observability” is more than a slogan for us. It’s an idea that informs our product roadmap and guides our problem-solving with customers. We’ve done a lot to explain network observability to prospects.
SD-WAN vs. MPLS
The real cost of latency
15 Best Linux Networking Commands and Scripts You Should Know
Both servers and software development use Linux. Today, Linux distributions are used by the vast majority of electronics and embedded systems. Worldwide, Linux servers make up about 90% of all internet servers. Additionally, the Linux kernel is used by around 80% of all smartphones. Today, every system in the world is linked via a network. Information exchange across systems requires network connectivity. Computer networking refers to communication over the internet as well as within a network.
From Client to Service Provider: Jess Walpole's perspective on N-able
It's not the plane, it's the pilot when it comes to running your business
Achieving Operational Excellence with N-able
Secure Cookies Using HAProxy Enterprise
My colleague Baptiste previously published an article on how to protect cookies while offloading SSL. I recently encountered a customer who wanted to achieve a very similar goal but using a more recent HAProxy Enterprise version. This post will explain the best practices for how to secure your cookies using HAProxy Enterprise.
Microsoft Teams Troubleshooting Performance and Connection Issues
MSPs are the epicenter of supply chain threats
Standardizing with N-central RMM and Cove Data Protection to grow our business
Managing a NOC with N-central
Don't put lipstick on a pig when it comes to backup
How to check bandwidth usage per IP
Handling today’s network performance challenges is imperative. Especially when there’s no specific tool for proactive monitoring, results from a root cause analysis are often incomplete. Organizations that don’t review metrics related to performance and availability risk compromising their network.
True Network Monitoring ROI Means Upgrading Your NetOps Strategies
Running network operations today is more complicated than ever before. Networks are growing in size and complexity due to modern network architecture adoption, but organizations are not hiring more staff to compensate for this increased complexity and demand. The prevailing mentality seems to be to do more with what you have.
Top Tip for MSPs in 2023 from N-able Chief Customer Officer
User Experience for Observability
Operator Connect or Direct Routing? Managing Microsoft Teams Phone Service Quality
10 Best Open Source Switch Port Monitoring Tools
Switch port monitoring is one of the most crucial facets of network management. It not only provides insights into network switch port status but CPU load, memory utilization, historical port utilization, and more. Investing in switch port monitoring improves network-related performance across your organization and optimizes port usage. As a result, you'll enhance security, reduce cybercrime, optimize networks, enhance compliance, and safeguard your entire IT infrastructure.
9 Best Open Source Network Monitoring Tools
Network monitoring is a critical component of your network management strategy that provides valuable insights into network-related problems which can affect your organization. When you monitor networks regularly, you'll mitigate risks like overloaded networks, router problems, downtime, cybercrime, and data loss. Network monitoring lets you: All successful companies invest in network monitoring tools that provide accurate insights into performance, speed, security, and productivity.
DX UIM 20.4 CU5: What's New and Why Upgrade
For DX Unified Infrastructure Management (DX UIM) customers, there are significant benefits to be gained by staying current with the latest releases—and that’s especially true now. The latest version, release 20.4 cumulative update (CU) 5, offers a significant number of enhancements and new capabilities. This new release provides teams with a number of advantages, including increased flexibility, improved operational efficiency, and enhanced insights.
SolarWinds Day October 2022 - Observability for All
The SolarWinds Platform
Kentik Market Intelligence just increased its IQ - introducing KMI Insights!
Early this year we launched Kentik Market Intelligence (KMI). If you missed it, KMI enumerates transit and peering relationships as well as produces rankings based on the volume of IP space transited by ASes in different geographies. Using tables and charts, KMI offers a global view of the internet out-of-the-box without any configuration or setup. KMI uses public BGP routing data to rank ASes based on their advertised IP space.
How to monitor Nginx
Are you interested in learning how to monitor Nginx? In this post, we'll show you all about how Nginx works and how you can use Hosted Graphite to monitor it. First, we'll read what Nginx monitoring is all about and how it can together work with Prometheus. Nginx, pronounced like “engine-ex”, is an open-source web server that, since its initial success as a web server, is now also used as a reverse proxy, HTTP cache, and load balancer.