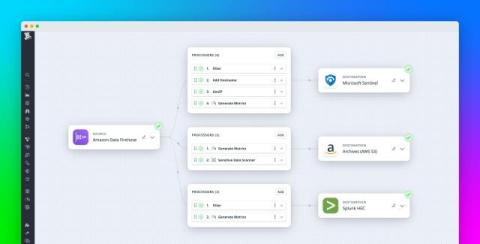
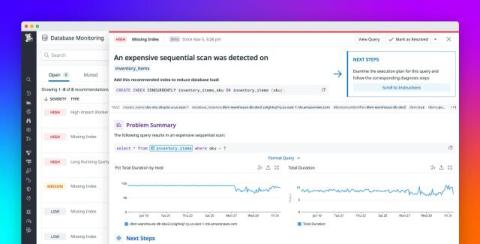
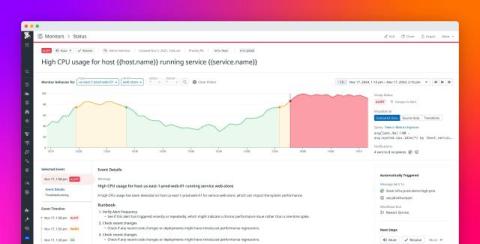
How Forbes delivers a premium digital experience with Datadog
Learn how Forbes, a global media powerhouse, successfully migrated to the cloud with Datadog. Discover how they enabled their teams across their entire tech stack to access IT data and make critical improvements. The team maintained a 99.5 percent uptime through proactive alerting and improved root cause analysis by 10 percent.