Operations | Monitoring | ITSM | DevOps | Cloud
August 2021
How to Do Simple UX Monitoring With ipMonitor
Testing Your HAProxy Configuration
Learn how to test your HAProxy Configuration. Properly testing your HAProxy configuration file is a simple, yet crucial part of administering your load balancer. Remembering to run one simple command after making a change to your configuration file can save you from unintentionally stopping your load balancer and bringing down your services.
Calico integration with WireGuard using kOps
It has been a while since I have been excited to write about encrypted tunnels. It might be the sheer pain of troubleshooting old technologies, or countless hours of falling down the rabbit hole of a project’s source code, that always motivated me to pursue a better alternative (without much luck). However, I believe luck is finally on my side.
Firewall... It's getting hot in here!
There’s something that humans and machines have in common, and no, it’s not the disappointment suffered by the final season of Game of Thrones, or, well, at least not only that. What we have in common is that we need protection. You know, animals need it too, and plants, but if you’ve gotten this far, it seems that you’re interested in computers, networks and all these pretty modern “geek” things, so today we’ll talk about that kind of protection.
What's in a Name? "Network Specialist" vs. "Network Engineer"
Why you should be using a VPN when working from home
With so many of us working from home full time for the last 16 months, VPNs have become essential tools for companies to keep their staff working in a safe environment. What we mean by “safe” is mainly about your online presence whilst performing daily tasks for your job.
Improving Web Page Load Time
HTTP/2 (originally named HTTP/2.0) was a major revision of the HTTP network protocol used by the World Wide Web published in 2015. Indeed, those in the Citrix/EUC ecosystem may remember Marius Sandbu investigating the benefits of HTTP/2 for NetScaler, Microsoft IIS, and Storefront users back in 2015/6. HTTP/2 was the first new version of HTTP since HTTP/1.1, which itself was standardized in RFC 2068 in 1997.
Value Stream Management Demo with ValueOps from Broadcom
Enreach acquires cloud solutions provider DSD Europe
The NetOps Expert - Episode 3: DX NetOps 21.2 Delivers Industry-Leading Network Monitoring Scale
Welcoming Scope Creep | An IT Journey to Monitoring Glory: Session 2
Is it All About the Brand? Yes and No!
Working for a company, you always want to think that your product or service is superior to the competition. As a Marketing executive, a major part of my job is to highlight why Ribbon is a leader in delivering IP Optical and Cloud & Edge solutions to the largest service providers, enterprises and critical infrastructure companies all over the world. But how do our customers perceive us? What do they really think of the Ribbon brand? How do we fare against our competitors in customers’ minds?
Ribbon and KGPCo Expand Partnership to Deliver Service Providers a Complete Portfolio of Cloud & Edge and IP Optical Solutions
How to Discover Devices and Connections With Engineer's Toolset
The HAProxy APIs
The HAProxy load balancer provides a set of APIs for configuring it programmatically. Although many people enjoy the simplicity of configuring their HAProxy load balancer by directly editing its configuration file, /etc/haproxy/haproxy.cfg, others want a way to do it without logging into the server. Or, they want a way that integrates with bespoke software. For example, they want to add pools of servers to the load balancer programmatically as a part of their CI/CD deployment pipeline.
What Is Network Traffic Analysis? A Helpful Walkthrough
Network traffic analysis is the method of collecting, storing, and analyzing traffic across your network. Traffic data is collected in or near real time so you can have up-to-the-second information about what’s happening. This allows you to take action immediately if a problem arises. You can also store this data for historical analysis.
What Is Network Traffic and How Do You Monitor It?
“Network traffic” is a term that describes the influx and outflux of network packets within an organization’s network. Understanding and monitoring this traffic is an important step in protecting an organization’s health. This blog post discusses what network traffic is, the different types, and how you can monitor it.
The Auvik Guide to Basic Switch Configuration
Maintaining Internet Privacy for Your Business
New Trends In Multi-Cloud Connectivity
7 email blocked list prevention practices for businesses
Email blocked listing is a major problem, but sometimes overlooked in the conversation around spam and email threat prevention . The impact on a business can be devastating if it isn’t caught in time, especially if the company relies on email marketing for lead generation and customer correspondence. While it’s possible to recover from the effects, it’s a complicated process and may set back productivity in the meantime.
Install HAProxy on Ubuntu
Learn how to Install HAProxy on Ubuntu 20.04. Ubuntu 20.04 is a great choice for installing your HAProxy software load balancer. It’s a free Linux operating system that’s fast, secure, and best of all, it’s easy to use. One of the features that makes Ubuntu so accessible to even the newest of users is its package manager, apt , the Advanced Packaging Tool.
Freedom without Order is a Sure Path to Chaos
Maximizing spectrum efficiency is a challenge that operators have wrestled with for decades. And the challenge of optimizing spectrum planning and management is only magnified as networks become faster and more complex. Operators with a well thought-out plan can avoid significant waste and inefficiency in the network. Wavelength division multiplexing was originally constrained to a fixed grid, first at channel widths of 100GHz, and then, as lasers improved, at 50GHz.
3 Sales tips to end the year strong
Happy New Year everyone! Don’t worry, I’m well aware it’s only August and we still have another four months or so before the “official” new year arrives. But with the winding down of summer and the commencement of the school year, I tend to view September as a type of New Year as well. September has always been my favorite month of the year.
Streamlining network operations with network management solutions
Networks today are moving towards increased agility and dynamic capabilities to support advanced networking requirements and business-critical processes. This causes the IT infrastructure to span across wireless, virtual, and hybrid environments as well. But with networks evolving quickly, IT admins have a hard time managing them without the right solutions in place.
What Is NaaS And How Can It Benefit Your business?
August/2021 - HAProxy 2.0+ HTTP/2 Vulnerabilities Fixed
If you are using HAProxy 2.0 or newer, it is important that you update to the latest version. A vulnerability was found that makes it possible to abuse the HTTP/2 parser, allowing an attacker to prepend hostnames to a request, append top-level domains to an existing domain, and inject invalid characters through the :method pseudo-header.
Getting started with Site24x7 NetFlow monitoring
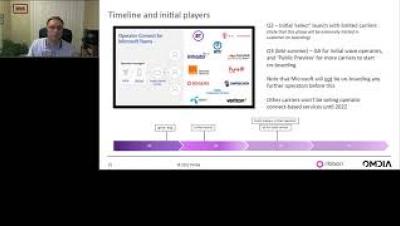
Microsoft Operator Connect
In March 2021, Microsoft announced Operator Connect, a new way for organizations to connect Microsoft Teams to a telecom provider. From an enterprise buyer’s perspective, Operator Connect delivers a new “apps store” type of experience to enable organizations to choose a telecom provider and connect Teams users to the PSTN from the Teams admin center. Equally important, Operator Connect enables a new set of menu-based user configuration tools within the Teams admin center.
With DX NetOps, Oil Firm Scales Remote Network Access for 60,000 Users
Like many in 2020, executives at this large oil and gas services company made the decision to have most employees work from home and to restrict all nonessential business travel in order to keep their employees safe. The company rose to this challenge at the very outset of the pandemic. A virtual private network (VPN) is the most common and secure way to provide access to company resources and data when employees are traveling or working remotely.
BSO announced as one of the first official global connectivity providers for the NSE International exchange
You Need NetOps
All You Need To Know About Peering
How to Run HAProxy with Docker
Can you run HAProxy as a Docker container? Yes! Did you even need to ask? Docker is ubiquitous these days and you’ll find that many applications have been Docker-ized; the HAProxy load balancer is no exception. Pardon the cliché, but HAProxy was born for this. As a standalone service that runs on Linux, porting it to Docker certainly seemed natural. Why would you want to run your load balancer inside of a Docker container? Are their performance penalties when doing so?
How we keep N-central updated and secure
Following the security issues in the MSP market over the past 24 months, our customers, who are understandably concerned, have been asking what we do to keep the N-central® appliance (hosted or on-premises) updated and secure for them. I will do my best in this short article to outline how our engineering team keeps up with security. Please note this is valid as of the time of writing, but can change at any point.
Together with N-able, Dufeu transforms business through automation
Local Survivability for Microsoft Teams Phone System - Beyond Using Your Mobile Phone
The real-world use cases for deploying a Microsoft Direct Routing Survivable Branch Appliance (SBA)
INFRA:HALT 14 New Security Vulnerabilities Found in NicheStack
Baystate Health Employs DX NetOps to Manage Pandemic-Related Demand and Ensure 100% Network Availability
As we all know, the pandemic changed everything, from the way we shopped to the way we received healthcare. It introduced a whole new way to interact with healthcare professionals for yearly check-ups, consultations, and more. The pandemic also put the network in the spotlight as a critical method to deliver reliable applications experiences. All, if not most medical professionals used the telehealth application as one of the only ways to provide quality patient care.
How Should an MSP Evaluate a PSA Solution?
Managed services providers (MSPs) juggle a lot of responsibilities. They have to address rapidly changing customer demands while still providing high-quality service, managing increasingly complex environments, evolving their service offerings, and much moreyou’re your business scales, it’s hard to accomplish these goals without the help of professional services automation (PSA) software.
Curb network incidents fast with cross-domain correlation analysis
For many CSPs, increasingly complex networks and immature technological solutions result in a typically long time to the detection and resolution of incidents that impact the customer experience, the brand’s reputation, and the bottom line. With RAN, Mobile and IP core, transport and applications and dozens of other integrated components, the network is one of the most complex areas to monitor.
The NetOps Expert - Episode 2: DX NetOps Expands Observability for Even More SDx Technologies
6 Most Common Network Problems
Intermittent network problems frustrate users, affect productivity levels, overwhelm your IT team, and are a pain for network administrators to solve. There are many problems that can affect network performance, and some of them are very complex to identify and understand. To help you proactively identify network problems that may be plaguing your network, we’re running you through some of the most common network problems!
Why Should My Business Consider Private And Direct Connections To Huawei Cloud?
Kemp Flowmon ADS and Check Point Integration: Automated incident detection and response *full video*
Kemp Flowmon ADS and Check Point Integration: Automated incident detection and response
We have recently published a script for the integration of the Anomaly Detection System (ADS) with a Check Point firewall. This ensures automated threat detection and response where attackers are blocked from accessing the network resources and causing even further harm. The previous integration with Fortinet describes a way of stopping the attacker at the perimeter. The following use case is largely the same, except with a Check Point firewall instead.
Maximizing voice connectivity: Microsoft Teams and Zoom Phone BYOC
3 tips to enhance remote access security
As managed services provider (MSP) technicians know, remote access gives an authorized user the ability to enter another user’s computer or network through a network connection. This access is often established via a remote desktop protocol (RDP), which is a network communications protocol from Microsoft® that is specifically designed for remote management.
Less is more: Incident management and monitoring in hybrid IT infrastructures
Many companies are continuously modernizing their infrastructure – but there is no standard way for the perfect IT infrastructure. Still, hybrid architectures have become the status quo in enterprises. Almost all organizations have migrated at least parts of their assets to the cloud or run applications as cloud services. At the same time, businesses want to dovetail their IT architecture with software development and are therefore embracing dynamic infrastructures.