Operations | Monitoring | ITSM | DevOps | Cloud
Security
The latest News and Information on CyberSecurity for Applications, Services and Infrastructure, and related technologies.
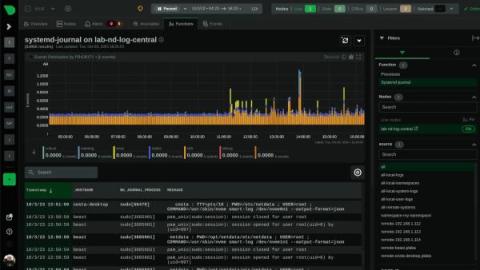
Improve Your Security With systemd-journal and Netdata
systemd journals play a crucial role in the Linux system ecosystem, and understanding the importance of the logs contained within is essential for both system administrators and developers.
Optimizing SharePoint Security
In today’s digital-first business landscape, collaborative platforms like Microsoft SharePoint are not merely a convenience but a necessity. They facilitate seamless interaction, information sharing, and collective project management across geographically dispersed teams. However, the enhanced connectivity and accessibility come with a set of security challenges.
How Hackers Use Unexpected Skills
Patch Management vs. Vulnerability Management: What's The Difference?
Leveraging Tines and Cribl Search for Security Automation
At Cribl, we have the privilege of helping our customers achieve their strategic data goals by giving them visibility and control over all of their observability data. The reality today is that data is commonly stored across many places. Whether intentional (such as using Cribl Stream to create a security data lake) or unintentional (because of silos and tool sprawl), organizations desire the ability to access and analyze all of this information at any time.
What Are Network Security Devices?
Find out about different network security device types and their uses.
Why Every Business Needs a Technology-Driven Protection Plan
The red team: ServiceNow's first line of defense
If you ask any ServiceNow employee about their role, they'll likely tell you their job and team are the best they’ve ever had. One small but mighty team proclaims this proudly: the red team, a group of professional hackers. As vigilant guardians of the company, the six-person team is tasked with testing the security of our systems and identifying cyber risks, data vulnerabilities, and security threats.