Struggling With Your Patch Management Process? Template, Essential Steps & Tips for a Stress-Free Patch Management Procedure
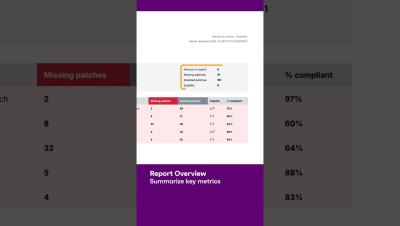
A patch management process lays out the steps associated with updating software and hardware. The typical patch management procedure includes things like prioritizing important patches, testing them, and eventually deploying them on an automated schedule — but with so many tools for managing patching in so many different kinds of setups, no two IT teams’ patch management processes look alike. What does your patch management process look like?