To SIEM or not to SIEM?
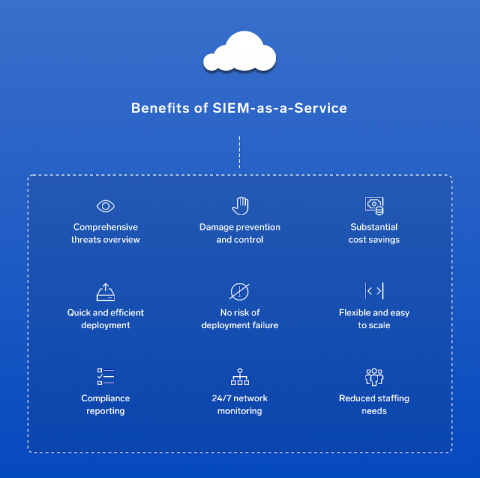
Not investing in Security Incident and Event Management solutions means you’re missing out on significant business benefits. SIEM detects and responds to security incidents in real time, which reduces the risk of noncompliance. It also helps realize greater value across all underlying security technology and systems. Reporting with SIEM is more comprehensive and less time-intensive, helping to reduce capital and operational costs through consolidation.