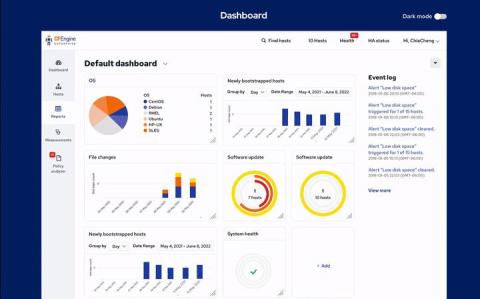
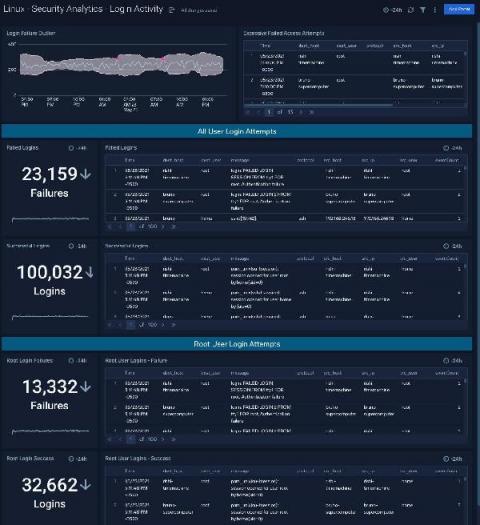
The CFEngine UI gets a fresh look
In the past 2 and half months, we have refreshed the visual design of the CFEngine Mission Portal. You might already notice some differences in the navigation, iconography, and color set. This is a post to guide you through the major changes we made and also provide you an inside perspective into the design direction we are taking going forward.