Secure Factory: Time to Step Up for the Manufacturing Industry
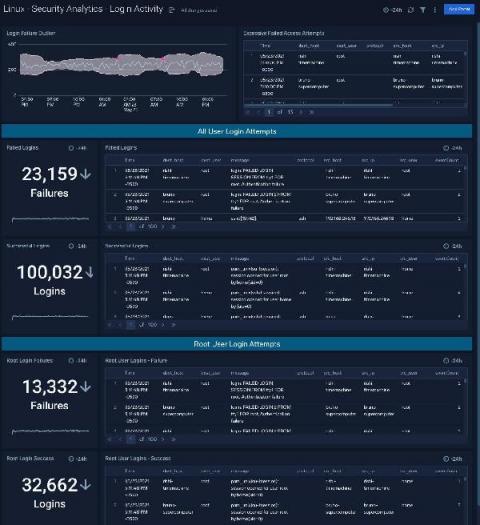
The ongoing news of massive cyberattacks on manufacturing and energy companies has been a wake-up call. Operational Technology (OT) Security had not been on the radar of many CISOs and plant managers until they got hit. After reacting in a defensive mode last year it is time to step up with a proactive security strategy including OT. Secure Factory by Splunk helps manufacturing companies better understand and address their unique security challenges.