Operations | Monitoring | ITSM | DevOps | Cloud
Technology
The latest News and Information on APIs, Mobile, AI, Machine Learning, IoT, Open Source and more!
With 36M+ Downloads, VictoriaMetrics Skyrockets to New Heights: 2021 in Review
We took advantage of the quiet days between holidays to look back on the year past and thank our users and customers for their support in 2021 - and wish you a very happy 2022!
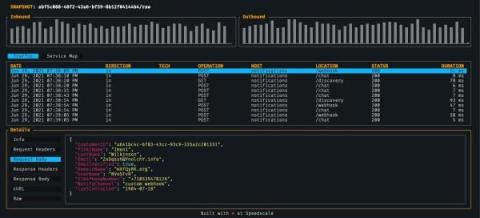
Speedscale Launches CLI: Free API Observability Tool
We are excited to announce the launch of Speedscale CLI, a free observability tool that inspects, detects and maps API calls on local applications or containers. The offering underscores the importance of continued and proactive API testing to quickly detect and debug defects within a shifting array of upstream and downstream interdependencies.
Build more resilient mobile apps with Flutter Crash Reporting
Powered by the Dart language, Flutter is one of the fastest-growing cross-platform programming frameworks in the world. Since its release in 2017 it has been empowering developers to build mobile apps that work seamlessly across iOS and Android with a single code-base. If you're a Flutter developer, you'll already know the importance of building better quality software, faster - after all, it was made for that very reason. That's why today, Raygun is proud to bring you Flutter support Crash Reporting. This highly requested release gives you complete visibility into the health of your Flutter applications, with rich diagnostics that take you to the root cause of errors and crashes.
DevOps in the enterprise
Intro to Telegraf
What we've been reading in December (2021)
🎉 Happy 2022 everyone! 🎉 Here are the articles, videos, and tools that we’ve been excited about this December. We hope you enjoy these links, and we look forward to hearing what you’ve been reading in the comments or on the Interrupt Slack.
IoT's Importance is Growing Rapidly, But Its Security Is Still Weak
The weakest link in most digital networks is the person sitting in front of the screen – the defining feature of the Internet of People (IoP). Because that’s where, through cunning and manipulative tactics, unsuspecting recipients can be tricked into opening toxic links. Little do they know, however, they’ve unwittingly opened the gates to digital catastrophe. Of course, I have nothing against people. In fact, some of my best friends are people!