Telecommunications giant reveals an Active Directory server breach. What can we learn from it?
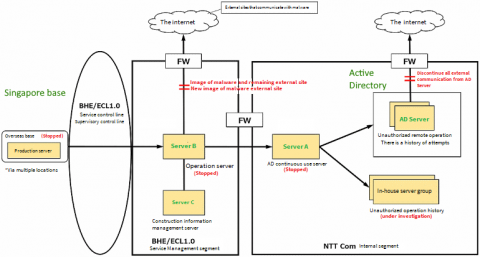
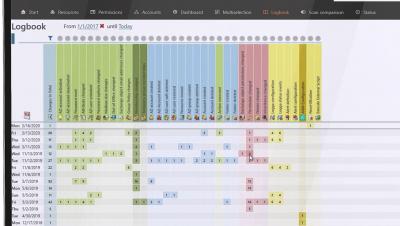
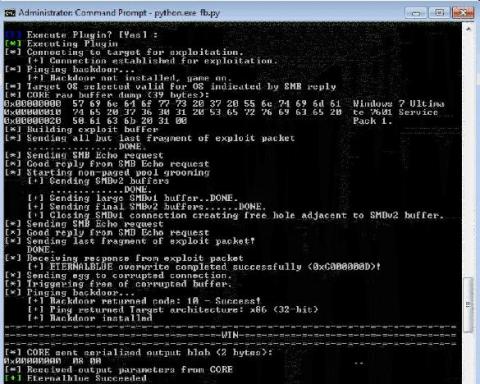
We’ve always been vocal about the imminent threat of breaches and propagated the message that irrespective of the size of your business, the industry you’re in, or your geography, you can be subject to a security breach. And unfortunately, history repeats itself often. On May 11, 2020, Nippon Telegraph & Telephone (NTT), a large telecommunications company, revealed that attackers may have stolen data from its internal systems, affecting over 600 customers.