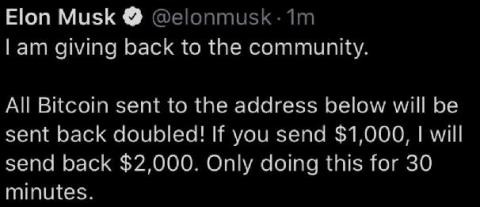
Enable TLS with Let's Encrypt and the HAProxy Kubernetes Ingress Controller
The HAProxy Kubernetes Ingress Controller integrates with cert-manager to provide Let’s Encrypt TLS certificates. When it comes to TLS in Kubernetes, the first thing to appreciate when you use the HAProxy Ingress Controller is that all traffic for all services travelling to your Kubernetes cluster passes through HAProxy. Requests are then routed towards the appropriate backend services depending on metadata in the request, such as the Host header.