Data Loss Prevention and Security Basics You Need to Know
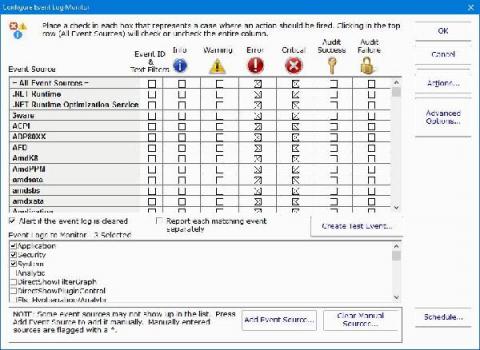
Cyberattacks are the “buzz word” that you hear when a company’s data has been breached. Sometimes the breach results in data being released on the internet. Other times, the hacker holds the data ransom in exchange for a large monetary payout. Data loss prevention and protection should be at the top of your list. Your data, after all, should be considered one of your most valuable business assets.