SecOps Is Getting Real (Time)
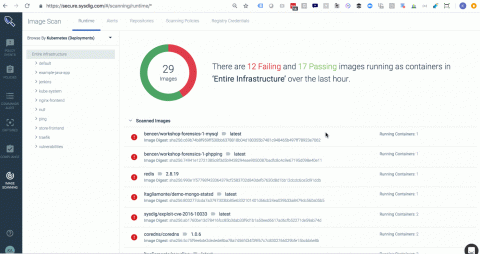
Companies migrating to the cloud need to ensure they have a strong security posture and can meet compliance requirements. Along with ensuring compliance, companies also are faced with the challenge of tying together multiple security tools that generate a high volume of event data across disparate interfaces and platforms. To help address this challenge, a new security service was introduced at AWS re:Invent 2018: AWS Security Hub.