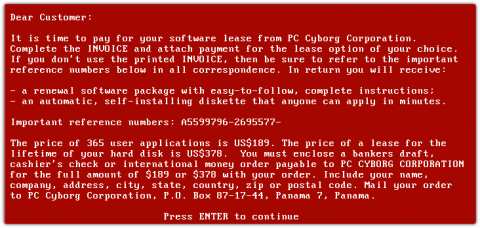
Battle the Ransomware Scourge with Deep Network Insight
Ransomware is the gift that keeps on giving. Old as it is (33 years) ransomware is constantly morphing into new exploits. The reason is simple. Ransomware works and too often cybercriminals walk away with bags of money (or piles of Bitcoin, anyway). “Following the World Health Organization's AIDS conference in 1989, Joseph L. Popp, a Harvard-educated biologist, mailed 20,000 floppy disks to event attendees.