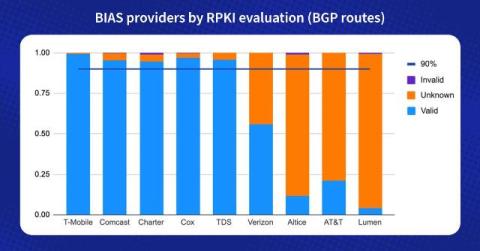
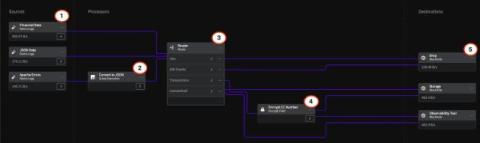
Ensuring Safety: Best Practices for Two-Way Secure File Sharing
In today's digital age, sharing files securely is crucial for protecting sensitive information. Whether you're transferring documents within a company or exchanging data with external partners, secure file sharing ensures that your data remains confidential and intact. This article explores the best practices for two-way secure file sharing to safeguard your information from unauthorized access and cyber threats.