Operations | Monitoring | ITSM | DevOps | Cloud
Latest News
Continuous Intelligence for Atlassian tools and the DevSecOps Lifecycle (Part 2)
The missing link to comprehensive endpoint security
Very few things available online are truly free of cost. If you don’t pay with cash, chances are you are paying with your personal information or other data. The Chrome web store is filled with free extensions that users install on their browsers to enhance their online experience. However, more and more of these extensions are being discovered and removed from the store due to their malicious intent.
Preventing "copy-paste compromises" (ACSC 2020-008) with Elastic Security
The Australian Cyber Security Centre (ACSC) recently published an advisory outlining tactics, techniques and procedures (TTPs) used against multiple Australian businesses in a recent campaign by a state-based actor. The campaign — dubbed ‘copy-paste compromises’ because of its heavy use of open source proof of concept exploits — was first reported on the 18th of June 2020, receiving national attention in Australia.
What is SIEM?
SIEM (Security Information and Event Management) is a kind of software whose purpose is to provide organizations and corporations with useful information. “About what?” you may wonder. Well, about potential security threats related to your business networks. SIEM does this through data collation and by prioritizing all kinds of dangers or threats. In general, we already answered the question “what is SIEM?”, but how does it do it?
The Path of an Outlaw, a Shellbot Campaign
Detecting Malware and Watering Hole Attacks with Splunk UBA
You may be surprised to learn that a particular malware is responsible for data theft in over 20% of financial institutions and other verticals in 2019. Watering hole attacks involve a web server that hosts files or applications where the website or files on the site become weaponized with malware. While recent news cycles have shined a spotlight on ransomware and crimeware, malware is not a new concept.
Protect Your AWS Infrastructure with GuardDuty and Coralogix
Cloud environments like AWS can be a challenge for security monitoring services to operate in since assets tend to dynamically appear and disappear. Making matters more challenging, some asset identifiers that are stable in traditional IT environments like IP addresses are less reliable due to their transient behavior in a cloud service like AWS. Amazon GuardDuty protects your AWS environment with intelligent threat detection and continuous monitoring.
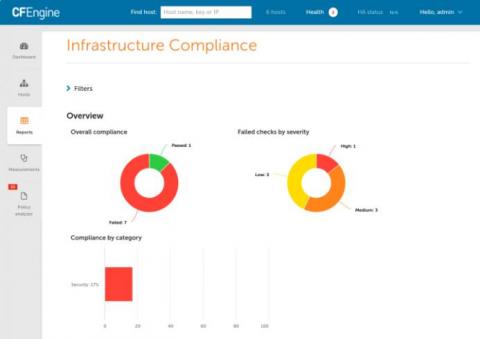
CFEngine 3.16 - Compliance
Today we announce the newest additions to CFEngine. CFEngine 3.16 brings several improvements, bug fixes, and new features. The theme for this release has been compliance, and it notably includes a new category of reports for proving compliance to regulation and other compliance frameworks in high level, easy to read reports. If you are interested to learn more about CFEngine, schedule training, or hear about pricing options, feel free to reach out to us!
The Importance of Monitoring SSL Certificates
Secure Sockets Layer, or SSL, is a global security standard technology that is being adopted by a number of different organizations across the globe. Essentially, SSLs are small data files containing a cryptographic key. This key carries important information about the organization using it. Around 600,000 websites have installed SSL certificates for security.