Operations | Monitoring | ITSM | DevOps | Cloud
Latest News
Improve network security with traffic filters on Elastic Cloud
Today we are pleased to announce new traffic management features for Elastic Cloud. Now you can configure IP filtering within your Elastic Cloud deployment on Amazon Web Services (AWS), Google Cloud, and Microsoft Azure. We are also announcing integration with AWS PrivateLink. These features help give you greater control over the network security layer of your Elastic workloads.
Practical security engineering: Stateful detection
Detection engineering at Elastic is both a set of reliable principles — or methodologies — and a collection of effective tools. In this series, we’ll share some of the foundational concepts that we’ve discovered over time to deliver resilient detection logic. In this blog post, we will share a concept we call stateful detection and explain why it's important for detection.
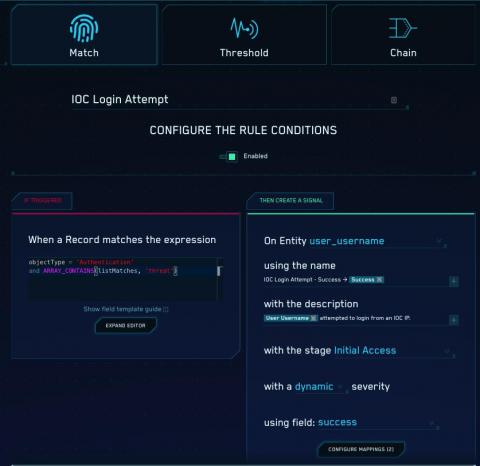
Cloud SIEM: Getting More Out of Your Threat Intelligence - 3 Use Cases for IOCs
Logging for DevSecOps
Logging is probably not the first item to come to mind when most of us think about DevSecOps, a term that refers to the integration of security into DevOps processes, but it should be. Logging and log management play a critical role in helping to put DevSecOps principles into practice by ensuring that developers, IT operations staff, and security teams have the visibility and communication pipelines they need to prioritize security at all stages of the DevOps delivery cycle.
How to Modernize Your Security Operations Center (SOC)
In an evolving world, the modernization of the security operations center (SOC) is pivotal to the success of digital transformation initiatives. Security teams, however, are facing a shortage of cybersecurity professionals and struggling to detect and prioritize high-priority threats. Analysts in data-driven organizations can combat these issues by bringing people, process and technology together.
Supercharged SOAR: Meet Splunk Phantom 4.9
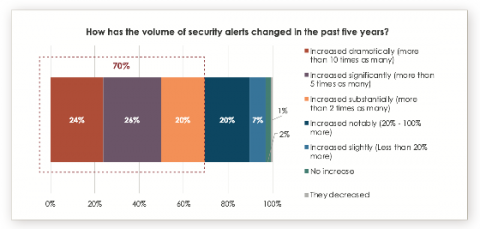
The number of cyberattacks launched on organizations continues to rise every year. More attacks means more security alerts that security analysts have to triage each day. Many security teams have turned to a security orchestration, automation and response (SOAR) tool to help them automate the ever-increasing volume of security alerts, and respond to threats faster and more comprehensively.
Five worthy reads: Embracing Zero Trust during a pandemic
Five worthy reads is a regular column on five noteworthy items we’ve discovered while researching trending and timeless topics. With the rising concern over cybersecurity in remote work, this week we explore the concept of the Zero Trust model in cybersecurity.