Operations | Monitoring | ITSM | DevOps | Cloud
Compliance
The role of SQL Monitor at Atruvia
4 Rising Trends in Enterprises: Cloud, Automation, Experience, and Compliance
When you’re running a business, you have a bunch of different tools and processes that you need to manage in order to keep everything running smoothly. It’s kind of like having a bunch of different puzzle pieces that you need to fit together just right in order to create a complete picture. Now, let’s say you want to take your business to the next level – maybe you want to expand your customer base, improve your productivity, or streamline your operations.
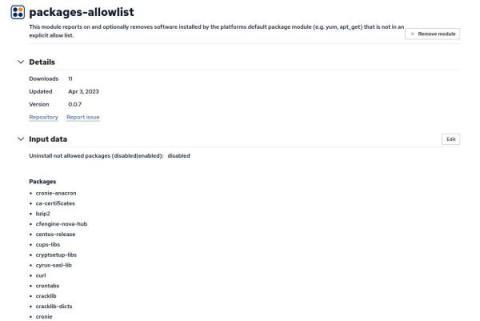
Improved software compliance with packages-allowlist
Having a list of software that is allowed to be installed on a host is a strategy to prevent and fix security gaps and maintain compliance with operational guidelines. This zero-trust methodology ensures that only explicitly permitted applications are allowed to be present on a host unlike package block-listing which enumerates an explicit list of software that is not allowed to be present. In fact, with a software allow-list, you are essentially block-listing everything except the software you allow.
Ubuntu compliance monitoring with Microsoft Intune
In recent years, data science, AI and software development have become a key focus area for organisations operating in every sector of the economy. This creates a pressing need to adopt Linux desktops in the enterprise, as research clearly shows a growing number of data scientists and developers prefer operating systems like Ubuntu.
Getting ahead of global regulations
In today’s world, the fitness of compliance and risk professionals is being tested like never before. Like the surfers who founded ServiceNow, we must find ways to get ahead of each new wave of federal and global regulations and ride as gracefully as we can—or wipe out. The key is to be proactive rather than reactive. No matter the regulation or resources at one’s disposal, the basic principles of establishing a strong compliance practice cannot be ignored.
Best CMMS Software Features and Its Benefits | Infraon
Reduce compliance TCO by using Grafana Loki for non-SIEM logs
Compliance is a term commonly associated with heavily regulated industries such as finance, healthcare, and telecommunication. But in reality, it touches nearly every business today as governments and other regulatory agencies seek to enact tighter controls over the use of our collective digital footprint. As a result, more and more companies need to retain a record of every single digital transaction under their control.