Migrating from Generic to Custom Attestations: A zero-trust approach to compliance
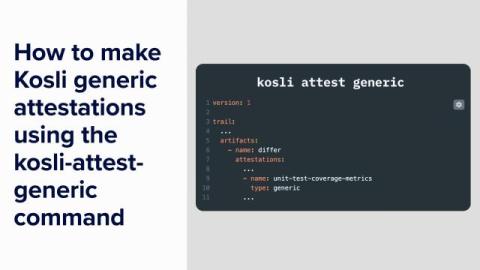
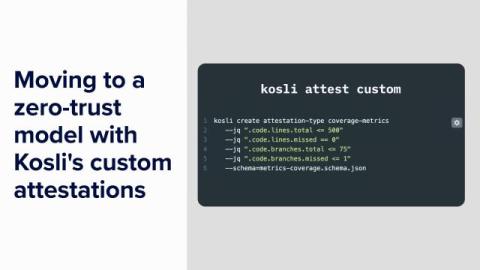
The kosli attest generic CLI command can attest anything, but unlike a “typed” attestation (such as kosli attest snyk), it does not calculate a true/false compliance value for you. Customers have reported that while a generic “escape hatch” is useful, it nevertheless has some drawbacks: Based on this feedback we’ve implemented a new attest command called kosli attest custom.