Advanced Active Directory attacks: Simulating domain controller behavior
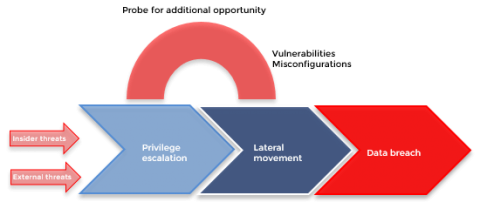
There was a time when cyberattacks on identity and authentication infrastructures [like Active Directory (AD)] were immensely challenging to perform. A lot of forethought had to be put into devising a plan for the careful execution of attacks, and advanced technical knowledge of domains and networks was a requisite. Over time, with the advent of open-source pen testing tools, the knowledge gap and the complexities involved to carry out a full-scale cyberattack have narrowed drastically.