Operations | Monitoring | ITSM | DevOps | Cloud
Security
The latest News and Information on CyberSecurity for Applications, Services and Infrastructure, and related technologies.
What is SOC 2 Compliance? | A Guide to SOC 2 Certification
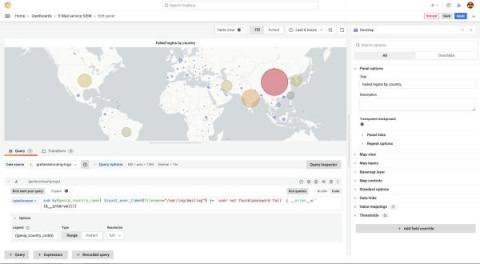
Protect PII and add geolocation data: Monitoring legacy systems with Grafana
Legacy systems often present a challenge when you try to integrate them with modern monitoring tools, especially when they generate log files that contain personally identifiable information (PII) and IP addresses. Thankfully, Grafana Cloud, which is built to work with modern observability tools and data sources, makes it easy to monitor your legacy environments too.
The Importance of Observability Pipelines in Gaining Control over Observability and Security Data
Today’s enterprises must have the capability to cope with the growing volumes of observability data, including metrics, logs, and traces. This data is a critical asset for IT operations, site reliability engineers (SREs), and security teams that are responsible for maintaining the performance and protection of data and infrastructure. As systems become more complex, the ability to effectively manage and analyze observability data becomes increasingly important.
Automatically manage keys and secrets on CircleCI
Data Shredding vs. Recycling: What's the Difference and Why Does it Matter?
6 Signs Your Company is Experiencing Data Breaches
Beyond Logging: The Power of Observability in Modern Systems
Empowering Security Observability: Solving Common Struggles for SOC Analysts and Security Engineers
5 Tips to Improve Network Security Monitoring
Optimizing network security monitoring requires pursuing continuous improvement. Even when people have monitoring tools or processes, it’s always advisable to identify weak spots and look for ways to reduce or eliminate them. Here are five options to consider.