How to Use Kentik to Perform a Forensic Analysis After a Security Breach
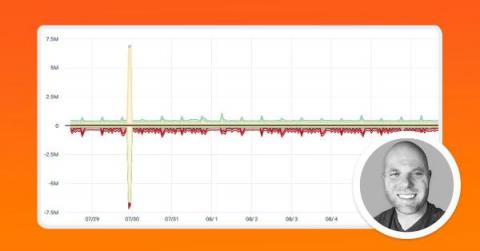
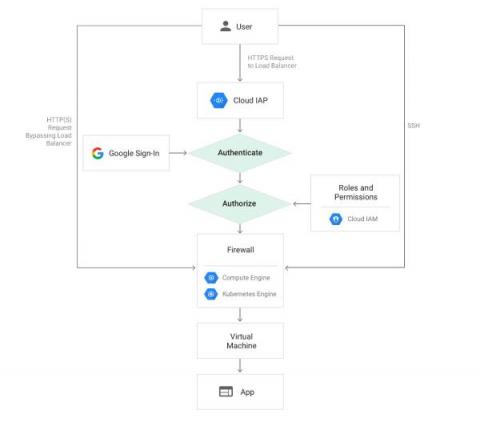
In this post, Phil Gervasi uses the power of Kentik’s data-driven network observability platform to visualize network traffic moving globally among public cloud providers and then perform a forensic analysis after a major security incident.