Operations | Monitoring | ITSM | DevOps | Cloud
Blog
In the aftermath of the SolarWinds hack, IT Ops leaders should reconsider on-premises tooling investments
Solarwinds is a 21-year old publicly traded monitoring and network management vendor with 300,000+ customers across the world. It’s familiar to IT operations and monitoring teams across enterprises big and small. And this week, it found itself in the news for all the wrong reasons.
Podcast: Break Things on Purpose | Ep. 11: Ryan Kitchens, Senior Site Reliability Engineer at Netflix
Get started with Gremlin's Chaos Engineering tools to safely, securely, and simply inject failure into your systems to find weaknesses before they cause customer-facing issues. We’re excited to kick off Season 2 of Break Things on Purpose next month. In anticipation of our next season, here’s a bonus show from our archives! Subscribe to Break Things on Purpose wherever you get your podcasts. Find us on Twitter at @BTOPpod or shoot us a note at podcast@gremlin.com!
A Few of Our Favorite Things: 2020 Resource Roundup
It’s that most wonderful time of year! Even though it’s been extra challenging for everyone, we can still take a breath, reflect on lessons learned, and look to fill our proverbial cups with knowledge to take into the New Year. We thought we’d revisit a few of our most popular Automation and AIOps resources from 2020.
Using Helm to Deploy a Kubernetes Application to Multiple Environments (QA/Stage/Prod)
One of the most typical challenges when deploying a complex application is the handling of different deployment environments during the software lifecycle. The most typical setup is the trilogy of QA/Staging/Production environments. An application developer needs an easy way to deploy to the different environments and also to understand what version is deployed where. Specifically for Kubernetes deployments, the Helm package manager is a great solution for handling environment configuration.
Using Mattermost as a tool for COVID-19 contact tracing
VCLB Ghent is a Belgian non-profit organization that serves pupils between the ages of 3 and 18 years old. Every two years, we offer students a free medical checkup. The organization also works with schools to support students that struggle with learning disabilities, behavioral problems, and other issues. As a multidisciplinary team, VCLB Ghent’s staff does contact tracing for schools in the event of an outbreak of a contagious disease, such as meningitis, hepatitis, or measles.
Generate Code Coverage Reports using Coveralls and Codefresh
Coveralls is a web service that allows users to track the code coverage of their application over time in order to optimize the effectiveness of their unit tests. Once you are managing your application and associated resources within a CI/CD platform like Codefresh, you want to receive insights on the test coverage automatically with every pipeline build. This post provides an overview of how this can be achieved with Coveralls and Codefresh.
How to perform a zero-downtime upgrade of Elasticsearch in production
Many users need their Elasticsearch clusters to always be available. And a lot of these same users also want to upgrade their Elasticsearch environment when a new version is released, so they can take advantage of all the new features and functionality. The result is that admins end up upgrading the Elasticsearch engine while it is operating at full capacity in production. Sound too good to be true?
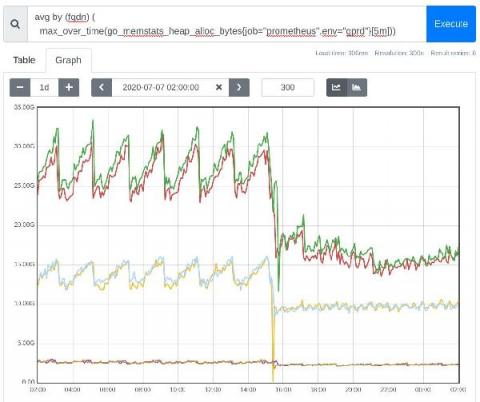
Prometheus 2020 year in review
It’s been a busy year in the world of Prometheus. Some of the 2020 highlights include a new agent; the addition of some great new features; new ways to reduce memory usage and have a faster restart time; and a fresh look at many old decisions and consensus positions.
New Vulnerability Exposes Kubernetes to Man-in-the-Middle Attacks: How to Mitigate CVE-2020-8554
A few weeks ago a solution engineer discovered a critical flaw in Kubernetes architecture and design, and announced that a “security issue was discovered with Kubernetes affecting multi-tenant clusters. If a potential attacker can already create or edit services and pods, then they may be able to intercept traffic from other pods (or nodes) in the cluster.” If a hostile user can create a ClusterIP service and set the spec.externalIP field, they can intercept traffic to that IP.