What Is IPv6? Definition & Full Overview
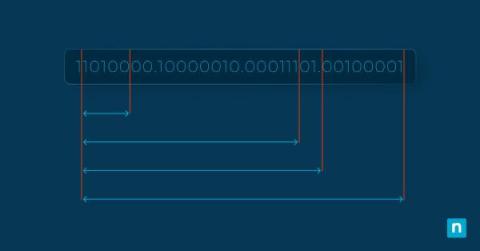
Poised to redefine the landscape of digital communication stands the groundbreaking achievement that is IPv6, the sixth generation of the Internet Protocol. The evolution from IPv4 to IPv6 marks a pivotal shift in internet technology, driven by the increasing scarcity of IPv4 addresses and the expanding scale of the global network.