Operations | Monitoring | ITSM | DevOps | Cloud
Security
The latest News and Information on CyberSecurity for Applications, Services and Infrastructure, and related technologies.
What's new in Kubernetes 1.20?
Another noteworthy fact of this Kubernetes 1.20 release is that it brings 43 enhancements, up from 34 in 1.19. Of those 43 enhancements, 11 are graduating to Stable, 15 are completely new, and 17 are existing features that keep improving. So many enhancements means that they are smaller in scope. Kubernetes 1.20 is a healthy house cleaning event with a lot of small user-friendly changes.
Security, compliance, and visibility for Amazon EKS-D
Today AWS unveiled the Amazon EKS Distro (EKS-D) and Sysdig is excited to deliver support for the new Kubernetes distribution with our Secure DevOps solutions. Wherever you choose to run EKS-D to run container applications, Sysdig can also be used to detect and respond to runtime threats, continuously and validate compliance, as well as monitor and troubleshoot.
Tigera to Support Amazon EKS-Distro
Today, we are excited to announce our commitment to support Calico and Calico Enterprise for the Amazon EKS-Distro, a Kubernetes distribution based on and used by Amazon EKS. EKS-D enables you to create reliable and secure Kubernetes clusters using the same versions of Kubernetes and its dependencies deployed by Amazon EKS. We view EKS-D as further confirmation of the central role that Kubernetes plays in today’s IT infrastructure.
Ivanti Acquires MobileIron and Pulse Secure to Accelerate Our Vision for the Everywhere Enterprise
I am excited to share the news that Ivanti has closed the acquisitions of MobileIron, a leading provider of mobile-centric Unified Endpoint Management (UEM) solutions, and Pulse Secure, a leading provider of secure access and mobile security solutions.
IT Life Hacks for Monitoring
COVID-19 Pushes Schools to Their Limit, and the Cloud Shows Its Worth
Event Log Management and Monitoring
Computer networks all around the world generate daily records of events occurring in their system. Some events are routine while others indicate potential security breaches or weak network health. Event log files consist of log information that can help organizations reduce their exposure against malware, intruders, damages and legal obligations.
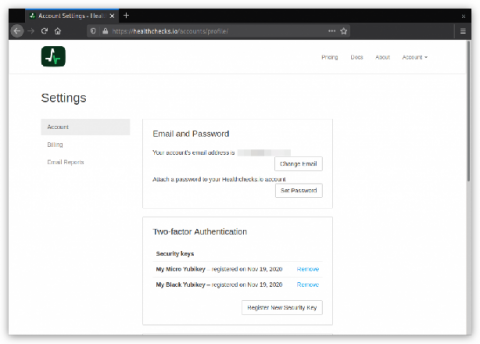
Two-factor Authentication
Healthchecks.io now supports two-factor authentication using the WebAuthn standard. Here is how it works: in the Account Settings page, users can see their registered FIDO2 security keys and register new ones.
5 Remote Working Best Practices and Tips in the Era of Coronavirus Pandemics
As the COVID-19 pandemic sweeps the world, the need has arisen for workers everywhere to adopt remote working practices wherever possible. Remote working presents many opportunities for both businesses and individuals to make better use of their time and enjoy a more streamlined approach to task delegation. Through the use of specialized software, such goals can be achieved without demanding more of individual team members or managers.