Securing Kubernetes clusters with Sysdig and Red Hat Advanced Cluster Management
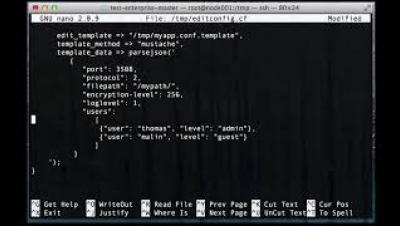
In this blog, we introduce the new integration between Sysdig Secure and Red Hat® Advanced Cluster Management for Kubernetes that protects containers, Kubernetes, and cloud infrastructure with out-of-the-box policies based on the Falco open-source runtime security project. Organizations are quickly growing their Kubernetes footprint and need ways to achieve consistent management and security across clusters.