Operations | Monitoring | ITSM | DevOps | Cloud
Security
The latest News and Information on CyberSecurity for Applications, Services and Infrastructure, and related technologies.
Securing Productivity in Supply Chains
Mobile device management – it’s been part of your operational technology portfolio for a long time. You’ve been using it for years – or maybe decades – to stage device configurations, push software updates and more. You might be using our Ivanti Avalanche MDM solution to manage your rugged mobile deployments. The device, OS and app management capabilities remain at the center of your mobility management program, and that isn’t going to change.
What is Ransomware?
Comparing Cybersecurity Trends Since the Pandemic
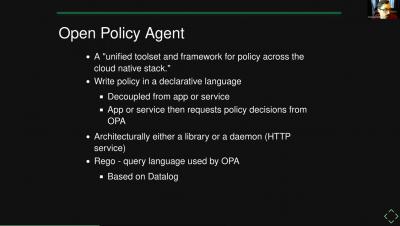
CFEngine: The agent is in 18 - Policy examples
Scary stories you won't believe until they happen to you!
For halloween this year, we wanted to share some scary scenarios along with security recommendations to help avoid them. All the names, companies and characters are made up, but the events and experiences are based on things which could happen, or have happened in the real world.
Show Notes: The Agent is In - Episode 18 - Policy Examples
Do you know how to use every function available in CFEngine? Join Cody, Craig, Herman to see how Nick uses org-mode, org-roam, and ob-cfengine3 to manage his personal collection of CFEngine Function Examples.
What Is MITRE D3FEND, and How Do You Use It?
MITRE is a world-renowned research organization that aims to help build a safer world. It is probably best known in the information security industry for being the organization behind the industry-standard CVE (Common Vulnerabilities and Exposures) list. Each entry on the list is supposed to include an explanation of how the vulnerability could be exploited. These attack vectors are tracked and defined in another well-known knowledge base called ATT&CK, which is also maintained by MITRE.
Seven steps to strengthen your security posture
Learn more about application security, why it matters and how to strengthen your security posture with these critical steps.