Operations | Monitoring | ITSM | DevOps | Cloud
Blog
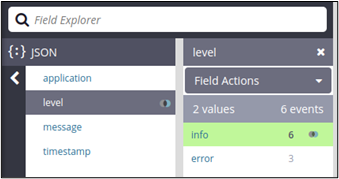
Effective Logging in Node.js Microservices
Cloud repatriation: What's behind the return to on-premises?
Find out why cloud repatriation is on the rise — and what makes on-premises the ideal approach for some businesses. Over the last ten years, the cloud has been touted as a game-changer. But, like magpies, have we all jumped on the “shiny object syndrome” bandwagon? Spending on public cloud services continues to show strong growth, with Gartner forecasting that by the end of 2023, worldwide end user spending on public cloud services will total nearly $600 billion.
Microsoft Dynamics Monitoring: CRM Performance Optimization
Microsoft Dynamics empowers enterprises with efficient customer relationship management (CRM) and enterprise resource planning (ERP) capabilities. As organizations increasingly rely on the seamless functioning of Microsoft Dynamics to drive their core processes, the need for robust monitoring practices has become paramount. This is where Microsoft Dynamics Monitoring steps into the spotlight, bridging the gap between uninterrupted productivity and potential disruptions.
Azure Key Vault: A Comprehensive Overview
Azure Key Vault is Microsoft’s dedicated cloud service, designed to safeguard cryptographic keys, application secrets, and other sensitive data. In an era where digital security is paramount, it functions as a centralized repository. Here, sensitive data is encrypted, ensuring that only designated applications or users can access them. Imagine having a hyper-secure, digital vault where you can store all your essential digital assets.
Building a Scripted Event Collector With Cribl Stream
Cribl Stream provides a robust HTTP REST collector, with many features and options. Still, there are endless combinations that vendors can provide in their API endpoints. Sometimes you may need to take more extreme measures to unlock data stashed begin the API entry point. No worries! Cribl also allows you to run a script to collect that data, and can even help you scale it. In this blog post, we’ll cover how I completed this task for a recent interaction using Qualys.
Mastering Network Monitoring: Your Guide to Uninterrupted Excellence
In the age of digital dominance, where every click and connection propels businesses forward, the lifeline of success lies in the seamless operation of computer networks. Imagine this: your website’s pulse is in perfect sync, applications running smoothly, and customers navigating without a second’s delay. This is where the art of network monitoring steps in, weaving the invisible threads that ensure unparalleled performance and uninterrupted excellence.
How generative AI is increasing cyber risk & what to do to make sure you're ready
Generative AI is all the buzz these days with the popularity of platforms and tools such as ChatGPT, Bard, Scribe, Jasper, and others experiencing exponential growth. This is a technology that has come to the fore with the force of a runaway train that’s bringing us head long into the future at the speed of light. It is transforming everything we do from writing code to making travel plans. And cybersecurity is no exception.
Using Argo CDs new Config Management Plugins to Build Kustomize, Helm, and More
Starting with Argo CD 2.4, creating config management plugins or CMPs via configmap has been deprecated, with support fully removed in Argo CD 2.8. While many folks have been using their own config management plugins to do things like `kustomize –enable-helm`, or specify specific version of Helm, etc – most of these seem to have not noticed the old way of doing things has been removed until just now!
Reliably receive a call when an organ donor is matched
Within the broader context of organ transplantation, time is of the essence. Lives hang in the balance, waiting for that life-changing call announcing a matched donor organ. For organ transplant recipients, the waiting game is often a test of patience and resilience. However, with the advent of modern technology, a solution has emerged to alleviate this uncertainty – OnPage.