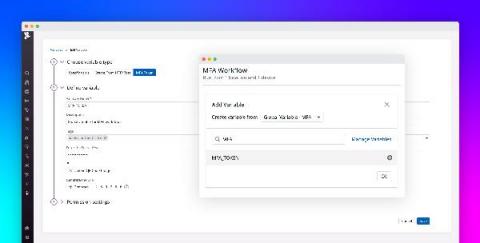
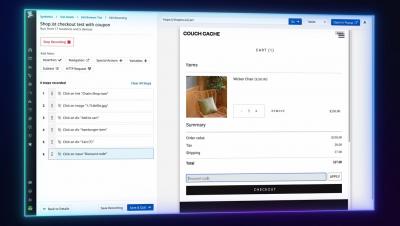
Test internal applications with Datadog's testing tunnel and private locations
As part of your monitoring and testing strategy, you may run tests on different types of applications that are not publicly available—from local versions of production-level websites to internal applications that directly support your employees. Testing each one requires leveraging tools that allow you to verify functionality across a wide range of devices, browsers, and workflows while maintaining a secure environment.