Operations | Monitoring | ITSM | DevOps | Cloud
Logging
The latest News and Information on Log Management, Log Analytics and related technologies.
Managing Your SIEM EPS License with Cribl LogStream
We see unfriendly customer practices all around in the SIEM space. For example, some major SIEM vendors use an Events Per Second (EPS) license model to monetize access to their tools. Typically, these vendors will drop data above the EPS license or stop data ingestion to incentive license compliance if you run over your EPS license. These license controls disrupt operations and risk enterprise security posture, which can cause chaos.
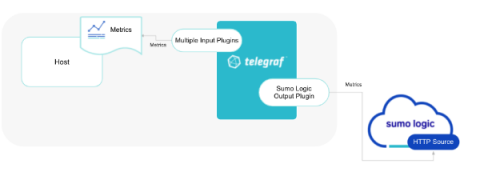
Host and process metrics - monitoring beyond apps
Micro Lesson: Metrics Formats Supported in Sumo Logic
Catching Malicious Log4j/Log4Shell Events In Real Time with LogStream
The recent Apache Log4j vulnerability CVE-2021-44228 dubbed Log4Shell is a big deal. By now there is no shortage of blogs, other write-ups, and analysis about why this vulnerability is an urgent issue and why there is a very good chance it applies to your environment. Here are some of the articles that dive into the gory details on this CVE.
Splunk Cloud Self-Service: Announcing The New Admin Config Service API For Private Applications
In our last blog, "Splunk Cloud Self-Service: Announcing the Admin Config Service (ACS)" we introduced our modern, cloud-native API that is enabling Splunk Cloud Platform admins to manage their environments in a self-service fashion. In this blog, we take a look at our latest effort to empower our customers: ACS private app management.
What is the Log4j 2 Vulnerability?
Over the last few days, there have been a tremendous amount of posts about the Log4j 2 vulnerability, with Wired going so far as claiming that, “the internet is on fire.” Tl;dr: LogDNA is not exposed to risk from the Log4Shell vulnerability in Log4j 2 at this time. If that’s all you came for, you can stop reading here. If you want to learn more about the vulnerability and how LogDNA protects you from risks like these, grab a cup of coffee and read on.
Observing Kubernetes With LM Logs
observIQ - Uber for Duckwalking
What are Linux Logs? How to View Them, Most Important Directories & More
In software, it’s essential to monitor logs of system activities. Today we’ll unravel what Linux logs are and how you can view them. Logging is a must for today’s developers and why Retrace was designed with a built-in, centralized log management tool.