Operations | Monitoring | ITSM | DevOps | Cloud
Blog
Common AzCopy Errors and How to Fix Them
AzCopy is a command-line tool provided by Microsoft to transfer data to and from Azure Storage services like Blob, File, and Table storage. It’s a vital tool for IT professionals who handle large-scale data operations, offering an efficient way to move data where it’s needed. However, as with any robust tool, users might encounter errors or issues while working with AzCopy. In this article, we’ll explore some common AzCopy errors and provide solutions on how to fix them.
Exploring distributed vs centralized incident command models
Recently in our Better Incidents Slack channel, there’s been some chatter around how people structure dedicated incident commanders at their company: distributed or centralized. The way I see it, there are two types of commanders: the temporary, distributed role — a hat that an on-call engineer or an engineering manager puts on during an incident. Then there’s the centralized, full-time role, where someone is the designated incident commander (or one of a few) for all incidents.
Why Andy Warhol would like - and dislike - AI
How to record a business process with Kosli's Audit Trail
Have you ever needed to provide proof that a critical business process actually took place? It’s a painful process involving all kinds of paperwork, but it’s the reality for many organizations working in highly regulated industries. For these companies, records need to be kept for actions like the provisioning of user accounts and access to sensitive records. It’s necessary, but it’s manual and time-consuming work.
Unraveling AWS Lambda: Exploring Scalability and Applicability
In our previous blog, we shared our firsthand experience of implementing a tracing collector API using serverless components. Drawing parallels with Amazon Prime Video’s architectural redesign, we discussed the challenges we encountered, such as cold-start delays and increased costs, which prompted us to transition to a non-serverless architecture for more efficient solutions.
BigPanda's Resources for Navigating Change Through the AI Revolution
AI has revolutionized the way we engage online in 2023. From Chat GPT and AI Art Generators to healthcare, finance, and business, you can hardly read the news without reading the latest proclamation of how AI is poised to change every aspect of our lives. AI has brought fundamental changes to how we live and work, and we’re still scrambling to understand the impacts of these changes. Especially where their work is concerned, change can be difficult for people to embrace.
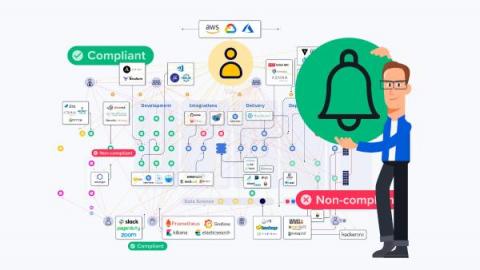
Stay on top of every change with Kosli Notifications
In this short blog, you will learn how to set up Kosli Notifications so your whole team can stay on top of environment changes and compliance events in real time. 🚀 In fast-paced technology landscapes, understanding how systems are changing is crucial. Developers, DevOps/Platform/SRE teams, security personnel, and management all need this information to manage operational risk, resolve incidents, and just for basic communication with each other.
Best tools for monitoring IoT devices
The security camera is one of the most prevalent IoT devices being used today. Ironically, one of these cameras' primary vulnerabilities is that they may be stolen or damaged - you need protection for the security cameras. Having gadgets that operate independently saves time since you may leave them to do the job they intended. However, remotely placed, unsupervised equipment must be monitored, and the most effective method is through the use of an automated monitoring system.