Operations | Monitoring | ITSM | DevOps | Cloud
Networks
The latest News and Information on IT Networks and related technologies.
OP5's network monitoring as an alternative to SolarWinds' Orion
An infamous cyberattack in late 2020 made SolarWinds a household name in the tech industry after it was discovered to be at the center of a supply-chain attack on its Orion network management tool. That attack allowed state-sponsored actors to push a malicious update to nearly 18,000 customers, including U.S. government agencies and about 100 large private enterprises.
Best practices for getting started with Datadog Network Performance Monitoring
Whether running on a fully cloud-hosted environment, on-premise servers, or a hybrid solution, modern services and applications are heavily reliant on network and DNS performance. This makes comprehensive visibility into your network a key part of monitoring application health and performance. But as your applications grow in scale and complexity, gaining this visibility is challenging.
New Hive Data Center Monitoring Agent
Obkio announces a new Monitoring Agent operated by Hive Data Center, a retail data center colocation provider based in Montreal, Quebec. Learn how Hive Data Center’s new Obkio Monitoring Agent will allow them to better support their customers and improve their quality of service.
Incident Review - What Was Behind the September 7 Spectrum Outage: A Case of Dr. BGP Hijack or Mr. BGP Mistake?
September 7, 2021, 16:36 UTC: an outage hit Spectrum cable customers in the Midwest of the U.S., including Ohio, Wisconsin and Kentucky. Users of their broadband and TV services hit social media to voice their annoyance at the disruption it was causing. Everything was resolved at around 18:11 UTC, and services were restored to users.
All You Need To Know About HAProxy Log Format
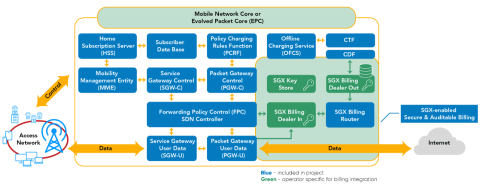
Evolution of Open-source EPC - A Revolution in the Telecom Industry
Open-source projects gravitate to some common problems in the industry. The use of open-source projects accelerates product/solution development and cuts down the costs. Open-source projects for embedded systems to the cloud are commonplace.
Rate Limiting with the HAProxy Kubernetes Ingress Controller
Add IP-by-IP rate limiting to the HAProxy Kubernetes Ingress Controller. DDoS (distributed denial of service) events occur when an attacker or group of attackers flood your application or API with disruptive traffic, hoping to exhaust its resources and prevent it from functioning properly. Bots and scrapers, too, can misbehave, making far more requests than is reasonable.
Painting a Complete Network Monitoring Picture: Why Context is Critical
In order to produce their masterpieces, artists like van Gough, Rembrandt, Picasso, and Monet painted with more than just one color. Being able to choose from multiple colors (not to mention an abundance of talent, inspiration, and creativity) is what allowed these artists to see their complete vision come to life on canvas. However, if you’re relying on a single set of data to troubleshoot network issues, it’s like you’re stuck painting with one color.