Operations | Monitoring | ITSM | DevOps | Cloud
December 2018
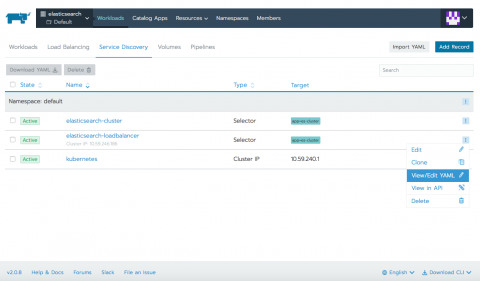
Deploying Elasticsearch Within Kubernetes
This tutorial walks through using Rancher to deploy Elasticsearch into a Kubernetes cluster. At the end of this article, you will have a fully functional 2-node Elasticsearch cluster, complete with sample data and examples of successful queries.
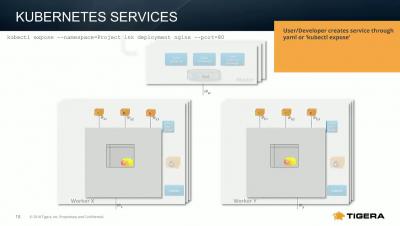
Leveraging Kubernetes Services & DNS
Top Takeaways from KubeCon + CloudNativeCon
Last week’s KubeCon + CloudNativeCon conference in Seattle proved yet again that Cloud Native computing is advancing at tremendous speed. Are you prepared to keep pace?
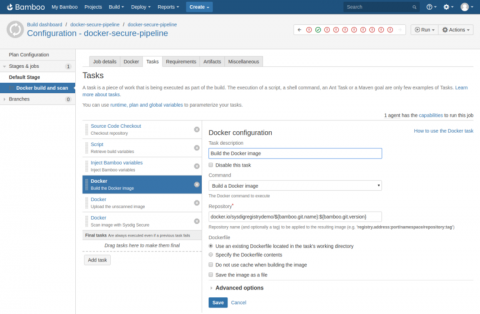
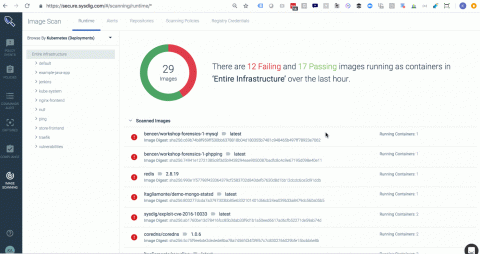
Integrating Sysdig Secure with Atlassian Bamboo CI/CD
In this blog post we are going to cover how to perform Docker image scanning on Atlassian’s Bamboo CI/CD platform using Sysdig Secure. Container images with security vulnerabilities or not compliant with the security policies that you define within Sysdig Secure will be stopped, breaking the build pipeline before being pushed to your Docker registry.
December 2018 Online Meetup Introducing Rancher's New Multi Tenant Prometheus Support
KubeCon 2018 + CloudNativeCon Recap
KubeCon + CloudNativeCon North America 2018 was an incredible event. We had many exciting announcements – LogDNA’s new partnership with IBM Cloud, our recent round of funding, as well as great conversations, product demos, fun giveaways, and even surprise gifts for loyal customers, our booth was jam packed.
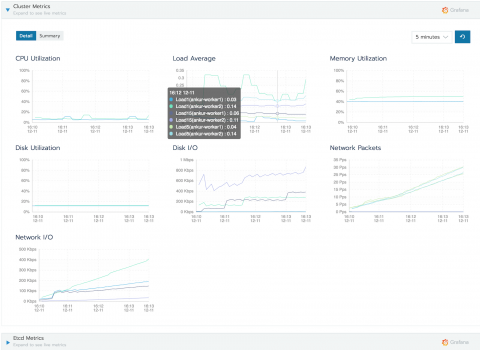
Monitoring Kubernetes, part 1: the challenges + data sources
Our industry has long been relying on microservice-based architecture to deliver software faster and safer. The advent and ubiquity of microservices naturally paved the way for container technology, empowering us to rethink how we build and deploy our applications. Docker exploded onto the scene in 2013, and, for companies focusing on modernizing their infrastructure and cloud migration, a tool like Docker is critical to shipping applications quickly, at scale.
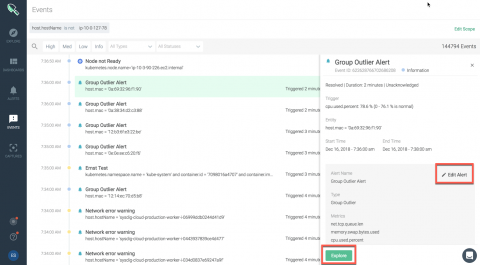
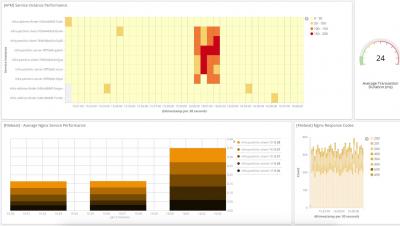
Unveiling Sysdig Monitor Events
At Sysdig, we have built a cloud-native intelligence platform to create a single, more effective way to monitor and secure your critical applications. We want to empower our users to quickly identify critical events and focus on events that need the most attention from you.
How to Make Kubernetes Work for Everyone
Intro to Kubernetes and Rancher Online Training - December 13, 2018
Dynamically Provisioning Local Storage in Kubernetes
At LogDNA, we’re all about speed. We need to ingest, parse, index, and archive several terabytes of data per second. To reach these speeds, we need to find and implement innovative solutions for optimizing all steps of our pipeline, especially when it comes to storing data.
Now Available: IBM Cloud Monitoring with Sysdig.
Today at Kubecon we announced the availability of IBM Cloud Monitoring with Sysdig. Together, IBM and Sysdig have launched this new offering to provide a fully managed enterprise-grade monitoring service for cloud-native applications on IBM Cloud. If you build, ship, and run applications on IBM Cloud, you now have direct, integrated access to Sysdig Monitor.
How to Get Started with Rancher's New Multi-Tenant Prometheus Support and Alpha Release Process
Ankur Agarwal, Rancher's Head of Product Management, describes new features in Rancher 2.2. Learn how to monitor multiple Kubernetes clusters in this step-by-step tutorial and how our Alpha Release process works.
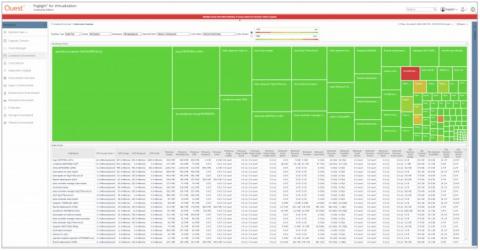
Foglight Container Management is available!
We’re excited to announce the general availability of a brand new product: Foglight Container Management – Part of the Foglight for Performance Management suite. oglight Container Management provides real-time and historical analytics of containers and their hosts, across physical, virtual and cloud environments. It identifies performance bottlenecks, failed containers and issues within the orchestration layer.
Upgrading Your AWS Kubernetes Cluster By Replacing It
With the recent panic over the zero-day Kubernetes vulnerability CVE-2018-1002105, Kubernetes administrators are scrambling to ensure their Kubernetes clusters are upgraded to a version that is patched for the vulnerability. As of this writing, the minimum versions that have the patch are 1.10.11, 1.11.5, 1.12.3, and 1.13.0-rc.1.
Kubernetes on the Edge
Today Rancher announces a partnership with Arm to create a Kubernetes-based platform for IoT, edge, and data center nodes, all powered by Arm servers. Rancher and Arm are working jointly on a Smart City project in China. Read more here.
Understanding the Impact of the Kubernetes Security Flaw and Why DevSecOps is the Answer
It finally happened. At the start of DockerCon Europe and a week before KubeCon was set to take place in the U.S., researchers discovered the first major vulnerability within Kubernetes, the popular cloud container orchestration system.
Infrastructure UI for Kubernetes and Docker using Elasticsearch and Kibana
Introducing Sysdig Secure 2.2: Kubernetes auditing, compliance, and access control.
Over the past four years we’ve helped hundreds of organizations run reliable, secure, and compliant Kubernetes and Openshift clusters. Some of the key themes we’ve seen from organizations that have successfully grown their Kubernetes footprint are: they have immaculate labeling, understand how to leverage internal Kubernetes features to harden their platform, and understand what developers need access to and manage it with RBAC and namespaces.
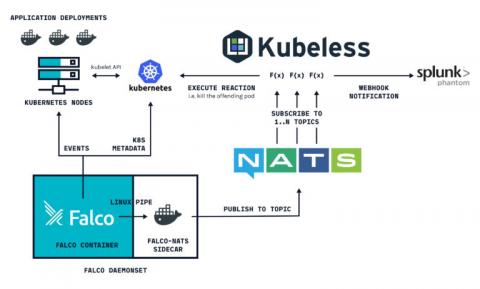
Container security orchestration with Falco and Splunk Phantom
Container security orchestration allows to define within your security policy how you are going to respond to your different container security incidents. These responses can be automated in what is called security playbooks. This way, you can define and orchestrate multiple workflows involving different software both for sourcing and responding. This is how Falco and Splunk Phantom can be integrated together to do this.
Istio - Enabling a Defense in Depth Network Security Posture
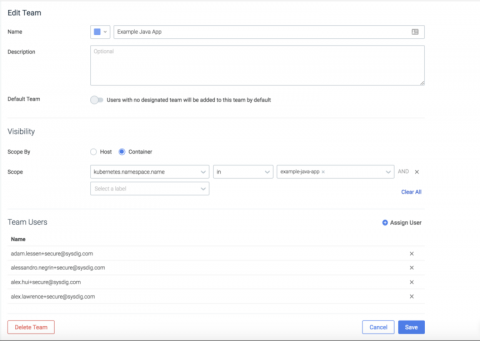
Service based access control with Sysdig Secure Teams
While you’re likely familiar with role-based access control, Sysdig teams introduce the concept of service-based access control. With service-based access control, administrators can define groups of users that have access to policy events, policy configuration, and scanning data limited to a service or set of services, as defined by your orchestration system (think Kubernetes, Mesos, and the like).
New container monitoring capabilities in Foglight for Virtualization 8.8.5
How to Monitor Kubernetes Without an Agent on Every Node
LogicMonitor is an agentless monitoring solution. What we really mean by “agentless” is that we don’t require an agent on every monitored server (physical or virtual). One LogicMonitor Collector - a lightweight application that takes just seconds to install - can monitor hundreds or even thousands of devices, including servers, virtual machines, network switches, storage systems, cloud resources, containers, and more.
Streamlined Kubernetes Cluster Agent
Sematext provides a single pane of glass and machine learning powered alerts for logs, metrics, traces and digital user experience data. The new Sematext agent is fully Docker Engine and Kubernetes-aware. (Re)written in Go, it has a minimal memory and CPU footprint. It also collects Kubernetes metrics in the most optimal fashion possible.
Kubernetes in Production: Services
We migrated all of our services to Kubernetes about six months ago. At first glance, the task seemed quite simple: deploy a cluster, write application specifications, and that’s it. But, since we’re obsessed with stability, we nevertheless had to learn how k8s works under pressure, so we tested multiple failure scenarios. Most of the questions that arose were network related. One particular point of concern was how Kubernetes Services function.
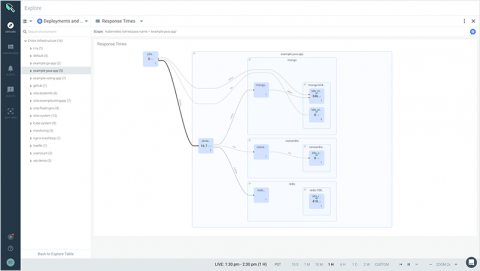
Introduction to Kubernetes Monitoring
Monitoring a Kubernetes cluster allows engineers to observe its resource utilization and take action when something goes wrong. This article explores what you should be monitoring and how to go about it with Rancher, Prometheus, and Grafana.
The Story of the First Kubernetes Critical CVE
Darren Shepherd, Rancher co-founder and Chief Architect, describes the Kubernetes critical CVE issue he discovered, how it came to a resolution, and what it says about the Kubernetes open-source community.
Hands Off My Docker Containers: Dynamic Java Instrumentation in Three Easy Steps
Instrumenting your application with an APM tool is not always easy. Configuration is often complicated, and managing agent files can be daunting. AppDynamics has developed a three-step solution for automating Java agent deployment and infrastructure monitoring in a Docker environment.
How to identify malicious IP activity using Falco
One of the most common security use cases, is the ability to identify connections generated by malicious actors, or internal components connecting to suspicious servers (e.g malware C&Cs). In this post, we will show how to leverage the Falco engine, to identify connections made to IPs that were flagged by multiple security sensors, and are streamed as a feed to the Falco engine.
Using Terraform for container security as code with Sysdig Secure
In the following tutorial you can learn how to implement container security as code. You probably have a CI/CD pipeline to automatically rebuild your container images. What if you could define your container security as code, push it into a Git repository to version control changes and then enforce your policy in your container orchestration tool like Docker or Kubernetes using Sysdig Secure?