Applying USB-based, Zero-touch Device Provisioning with NinjaOne
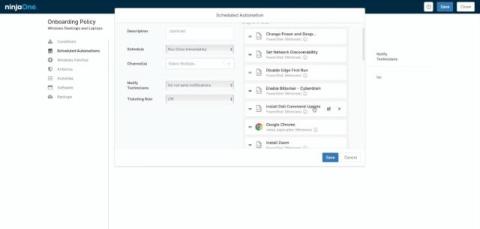
Modern provisioning in IT refers to defining your desired settings and software to meet your organizational goals. It’s the process of setting up your IT infrastructure, including hardware, networks, and virtual machines, among others, to make it available to systems and users. Device provisioning is a subset of this, often used to set up devices within the Internet of Things (IoT), including mobile devices. The importance of device provisioning cannot be overstated.