Operations | Monitoring | ITSM | DevOps | Cloud
Automation
Network automation tools and their importance in today's networks
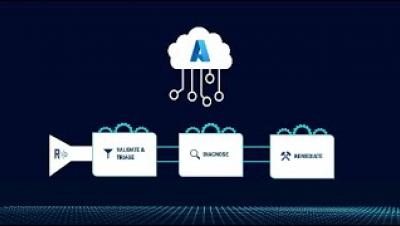
Resolve + Microsoft Azure Auto-Remediation Demo
CFEngine: The agent is in 18 - Policy examples
Scary stories you won't believe until they happen to you!
For halloween this year, we wanted to share some scary scenarios along with security recommendations to help avoid them. All the names, companies and characters are made up, but the events and experiences are based on things which could happen, or have happened in the real world.
Show Notes: The Agent is In - Episode 18 - Policy Examples
Do you know how to use every function available in CFEngine? Join Cody, Craig, Herman to see how Nick uses org-mode, org-roam, and ob-cfengine3 to manage his personal collection of CFEngine Function Examples.
What Is MITRE D3FEND, and How Do You Use It?
MITRE is a world-renowned research organization that aims to help build a safer world. It is probably best known in the information security industry for being the organization behind the industry-standard CVE (Common Vulnerabilities and Exposures) list. Each entry on the list is supposed to include an explanation of how the vulnerability could be exploited. These attack vectors are tracked and defined in another well-known knowledge base called ATT&CK, which is also maintained by MITRE.
Puppet by Perforce Announces Continuous Compliance for DISA STIGs
Resolve Systems' IT Automation SaaS Solution Available on Microsoft Azure Marketplace
Puppet supports DoD continuous compliance and configuration management
Puppet Enterprise now offers Compliance Enforcement Modules aligned to DISA STIGs Benchmarks. The Defense Information Systems Agency (DISA) Security Technical Implementation Guides (STIGs) were built to safeguard our most critical security systems and data against a dynamic threat environment, yet monitoring and enforcing widely deployed infrastructure at the U.S. Department of Defense (DoD) scale is a formidable task.