Operations | Monitoring | ITSM | DevOps | Cloud
Anomaly Detection
An Introduction to Anomaly Detection
In early 1900, Sakashi Toyoda invented a loom that automatically stops when the thread breaks, limiting the need for someone to watch the machine constantly. This approach was later named “Jidoka” and became one of the two pillars of the TPS (Toyota Production System) with just-in-time production representing the second pillar.
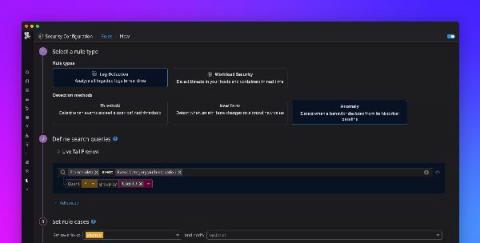
Detect security threats with anomaly detection rules
Securing your environment requires being able to quickly detect abnormal activity that could represent a threat. But today’s modern cloud infrastructure is large, complex, and can generate vast volumes of logs. This makes it difficult to determine what activity is normal and harder to identify anomalous behavior. Now, in addition to threshold and new term –based Threat Detection Rules , Datadog Security Monitoring provides the ability to create anomaly.
Preventing Shopping Cart Abandonment with Anomaly Detection
The global pandemic has changed B2C markets in many ways. In the U.S. market alone in 2020, consumers spent more than $860 billion with online retailers, driving up sales by 44% over the previous year.eCommerce sales are likely to remain high long after the pandemic subsides, as people have grown accustomed to the convenience of ordering online and having their goods – even groceries – delivered to their door.
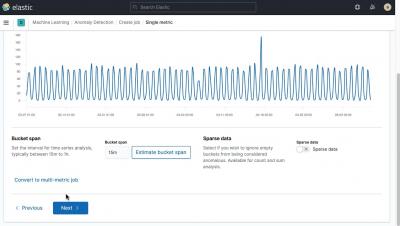
Anomaly Detection with Machine Learning
Science of Network Anomalies
Today’s networks have evolved a long way since their early days and have become rather complicated systems that comprise numerous different network devices, protocols, and applications. Consequently, it is practically impossible to have a complete overview of what is happening in the network or whether everything in the network works as it should. Eventually, network problems will arise.
Rethinking Anomaly Detection
Bridge the gap in your OSS by adding an AI brain on top
Telecom companies monitor their network using a variety of monitoring tools. There are separate fault management and performance management platforms for different areas of the network (core, RAN, etc.), and infrastructure is monitored separately. Although these solutions monitor network functions and logic – something that would seem to make sense — in practice this strategy fails to produce accurate and effective monitoring or reduce time to detection of service experience issues.
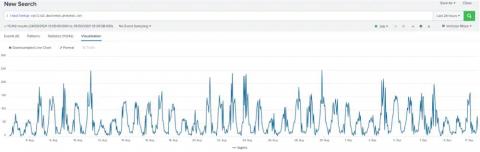
Exploratory Data Analysis for Anomaly Detection
Many of you might have seen our blogs about different techniques for identifying anomalies. Perhaps you even have a handful of analytics running in Splunk to identify anomalies in your data using statistical models, using probability density functions or even using clustering.