Operations | Monitoring | ITSM | DevOps | Cloud
Security
The latest News and Information on CyberSecurity for Applications, Services and Infrastructure, and related technologies.
12 Hybrid Cloud Security Threats That You Can Fix
Preventing malicious use of Weave Scope
Intezer and Microsoft reported on Sept. 9 that TeamTNT hackers are deploying Weave Scope in compromised systems as an auxiliary tool in their intrusions. Weave Scope is a legitimate and powerful tool to manage server infrastructure that, once deployed, makes it easy to control all resources. In this article, we will describe how this tool can be used maliciously, and how to add specific checks in your security set up to look for it.
Getting Up and Running with Calico for Windows
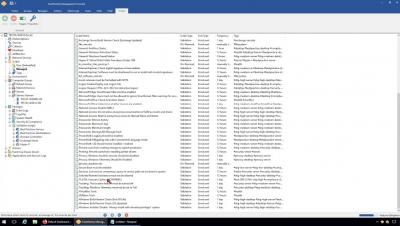
Getting started with EventSentry v4.2.x
See and Secure containers on AWS Fargate
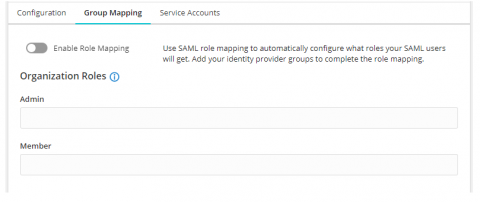
New SAML Group Mapping Support
Are You Ready for the New Opportunities?
2020 was a crazy year with tremendous disruption, hardship, and loss. While the pandemic brings social and economic chaos, it is also changing the very nature of how we live and work. This year we have seen a new wave of digital transformation amongst various business sectors and dramatic shifts in consumer behavior.
Create a New Integration in Opsgenie
Opsgenie is a powerful alert management service that allows you to flexibly set up teams for different alerting groups. Our development team have been working hard to deliver new features and integrations, and now you are able to integrate Opsgenie with RapidSpike to help with your website monitoring.
Elastic on Elastic: How InfoSec deploys infrastructure and stays up-to-date with ECK
This post is part of a blog series highlighting how we embrace the solutions and features of the Elastic Stack to support our business and drive customer success. The Elastic InfoSec Security Engineering team is responsible for deploying and managing InfoSec's infrastructure and tools. At Elastic, speed, scale, and relevance is our DNA and leveraging the power of the Elastic Stack is the heart of InfoSec.