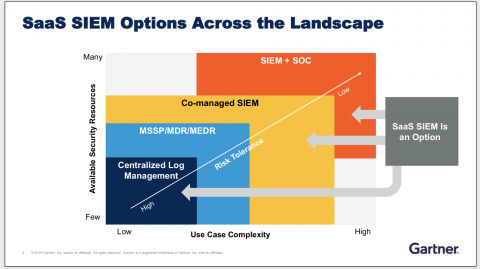
3 key takeaways on Cloud SIEM from Gartner Security & Risk Management Conference 2019
Gartner has been a thought leader in the SIEM space for the last few years. Gartner’s Magic Quadrant is considered one of the top market research reports on SIEM’s capabilities and vendors. Very recently, I attended the 2019 Gartner Security & Risk Management Conference, and based on thousands of conversations Gartner has had with their clients, they have a good vantage point on the SIEM space this year.