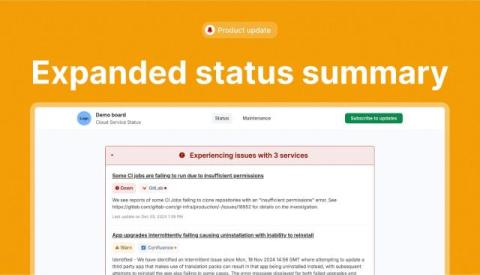
Top 5 outages detected by StatusGator in November 2024
StatusGator continues to demonstrate its value by providing early warning alerts for service disruptions, often detecting issues before official acknowledgment. Below, we highlight key incidents from November 2024 where StatusGator’s monitoring helped users stay ahead.