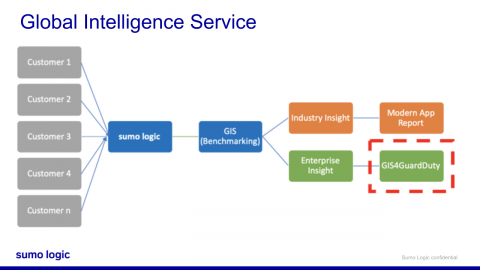
Benchmark your AWS security threats
Today, we are announcing the general availability of our new module within our Global Intelligence Service with a benchmarking capability on AWS security by baselining the Amazon GuardDuty findings. If you are one of the 100,000 users of Sumo, go to your App catalog and install the Amazon GuardDuty benchmark app with one click and see your threats against the global threats that we gather from hundreds of Sumo customers.