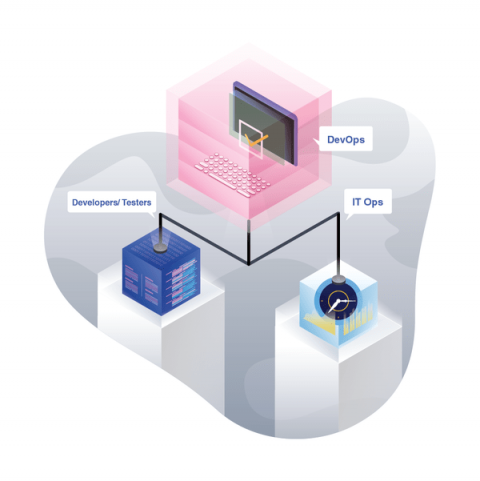
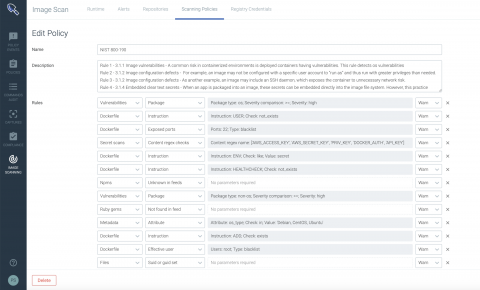
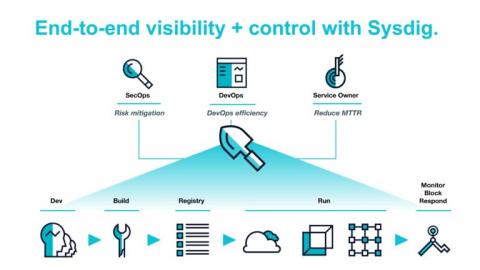
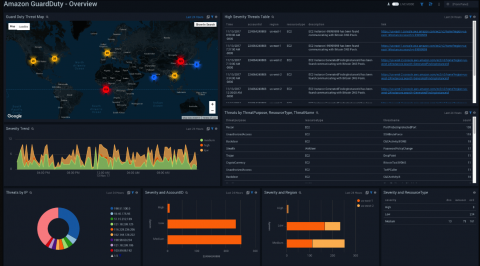
3 Steps to Implement DevSecOps in Your Organization
It seems like hardly a week goes by without news of a security breach. Cyberattacks are becoming more frequent and more severe, costing businesses $600 billion per year according to the 2018 Economic Impact of Cybercrime report. Without a strong security policy in place, businesses risk falling victim to new threats while losing the trust of their customers.