Raygun: It's time for time boards!
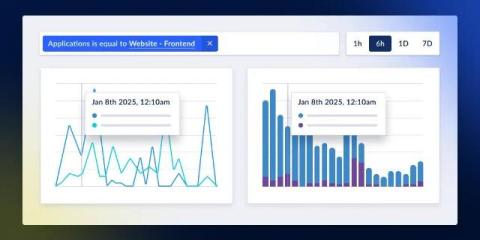
We’re excited to announce our latest feature, Timeboards, which will transform how you analyze your software issues and bottlenecks. This powerful enhancement to our dashboard system offers an alternate way to visualize your dashboard data by synchronizing time across all dashboard tiles.