Operations | Monitoring | ITSM | DevOps | Cloud
Latest Posts
New Integration: Create Zoom incident bridges automatically
Incident response doesn’t only happen in Slack, so today we’re happy to announce our integration with Zoom to create incident bridges automatically. Using the power of FireHydrant Runbooks, a Zoom meeting can be added with fully customizable titles and agendas based on your incident details. Let’s dive into how it works.
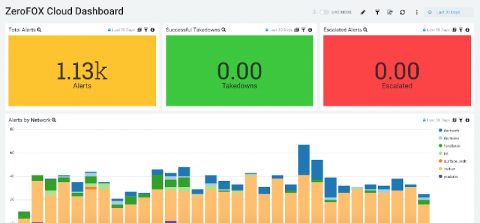
Sumo Logic and ZeroFOX Join Forces to Improve Visibility and Protect your Public Attack Surface
Through the Crisis: Nexthink Customer Stories (Philosophy at Work)
Dr. Brennan Jacoby is a philosopher and the founder of Philosophy at Work, an organization that works with businesses seeking to improve their thinking skills by leveraging great philosophers and philosophical techniques. In 2020, Dr.
Introducing LogDNA Web Server Template
With the ever-growing volume of application logs and analysis tools available, it can be time-consuming to set up your observability tools to keep up with best practices. Every new piece of infrastructure deployed also causes another piece of dashboard and monitoring that needs to be put in place to ensure stability and reliability.
Mitigate risk with rolling deployments
Deploying a new feature to production is a momentous occasion. It's important to ensure that everything goes properly at this stage, as deployments tend to be error-prone when not handled correctly. To examine why this is and how you can avoid it, let's take a look at the different types of deployments available and where some of them fall short.
How Playtech Fixed Metrics Over-Collection with Observability
According to Forbes, 2.5 quintillion bytes of data are created every day. Data volumes have grown exponentially in recent years due to the growth of the Internet of Things (IoT) and sensors. The majority of data collected has been collected in the last two years alone. For example, the U.S. generates over 2.5 million gigabytes of Internet data every minute, and over half of the world’s online traffic comes from mobile devices.
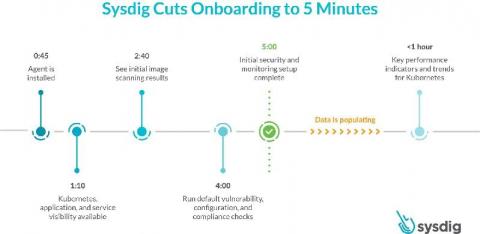
Sysdig Cuts Container and Kubernetes Visibility and Security Onboarding to 5 Minutes
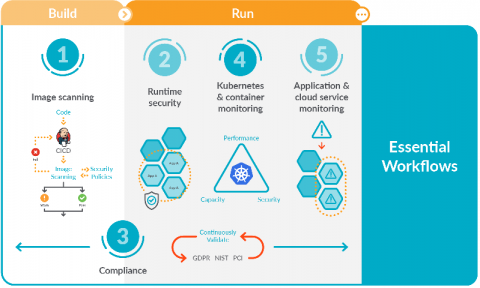
5 Essential workflows for secure DevOps
Focusing on these five essential workflows for secure DevOps will help you get started implementing monitoring, security, and compliance for containers and Kubernetes. You might be starting to adopt DevOps and find that it dramatically simplifies deploying applications in containers and Kubernetes. However, you probably also found that it adds a new set of complexities for managing, securing, and troubleshooting applications.
Sysdig cuts onboarding for container and Kubernetes visibility and security to 5 minutes
Today, we are excited to announce a faster onboarding for Kubernetes visibility and security. With the SaaS-first approach and new enhancements to the Sysdig Secure DevOps Platform, you can get results after just a five-minute setup. This release includes a new guided onboarding process, out-of-the-box dashboards as part of curated essential workflows, and a new Sysdig Essentials tier. 5 minutes to onboard secure DevOps - YouTube An error occurred.