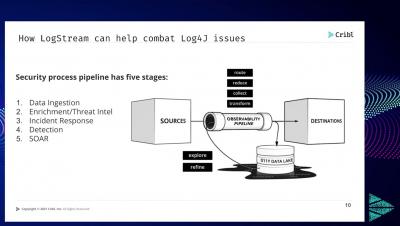
5 top hybrid cloud security challenges
Hybrid cloud environments can add complexity, reduce visibility, and require different logging and monitoring approaches for security teams. For a growing number of organizations, IT environments encompass a blend of public cloud services, private clouds, and on-premises infrastructure—with the latter becoming an ever-smaller portion of the mix. The past two years have seen a major uptick in the use of cloud services, and the trend shows no signs of slowing.