12 Days of Christmas Updates | Day Thirteen: Microsoft ILogger integration with Raygun
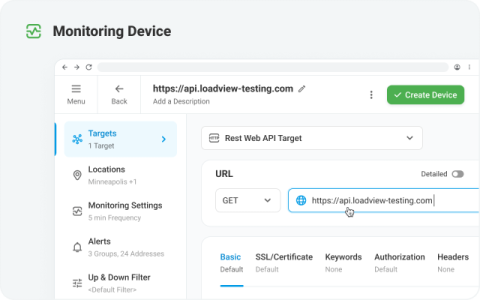
We've added support for Microsofts iLogger to the Raygun4Net provider. Now any exceptions logged with the iLogger are automatically sent to Raygun, no extra code needed!