How Sportsbet enhanced data security with automation
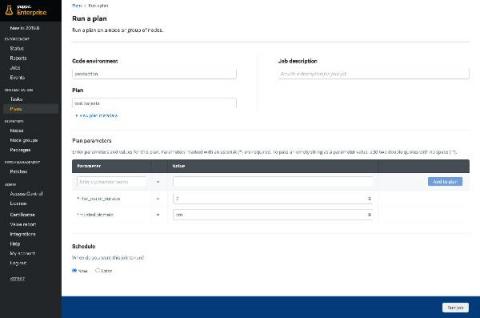
At Sportsbet, an Australian online betting company with more than 1.25 million customers, one thing we’re not willing to take a gamble on is customer security. That means having strict identity and access management protocols in place to protect customer data and get better visibility into whom our employees are and what they have access to.