Operations | Monitoring | ITSM | DevOps | Cloud
Vulnerability
Microsoft's Coordinated Disclosure Discussion from BlackHat & DefCon '22: Security Insights
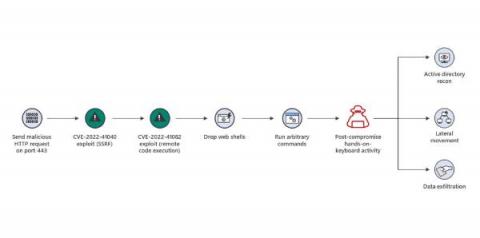
Microsoft Zero-Day Exchange Exploits Show Value of Network Behavior Visibility
There is no end to zero-day attacks. Lessen the pain by spotting them early. In recent days two zero-day vulnerabilities against Microsoft on-premises Exchange Servers have been publicized and exploited. The good news is that Exchange cloud users such as Microsoft 365 customers, need not worry as these exploits are only against the on-premises versions.
How to Manage Your Vulnerability Workflows with Cloudsmith
Scan your packages for vulnerabilities and never miss new vulnerabilities as they get discovered. Create actionable workflows by quarantining packages over defined vulnerability levels.
IBM Patches Severe Vulnerabilities in MQ Messaging Middleware
IBM this week announced patches for high-severity vulnerabilities in IBM MQ, warning that attackers could exploit them to bypass security restrictions or access sensitive information. Messaging and queuing middleware, IBM MQ provides enterprise-grade messaging between applications, enabling the transfer of data between programs and the sending of messages to multiple subscribers. Two security issues were resolved in IBM MQ this week, both residing within the libcurl library.
The Basics of Vulnerability Management
Code signing: securing against supply chain vulnerabilities
When creating an application, developers often rely on many different tools, programs, and people. This collection of agents and actors involved in the software development lifecycle (SDLC) is called the software supply chain. The software supply chain refers to anything that touches or influences applications during development, production, and deployment — including developers, dependencies, network interfaces, and DevOps practices.
Prevent XSS attacks with browser testing
Security is a never-ending battle on the web. You can have a server up in just a few minutes, and the next minute, someone is already trying to hack into it. These attacks could be automated using malicious bots or launched manually. Websites can be targeted by a malicious user trying to compromise your web presence or data. Cross-site scripting (XSS) is just one type of attack your site may be vulnerable to.
Supply Chain Security Meetup June 21 2022 (Sponsored by JFrog)
Follina Zero-Day Vulnerability: Overview and Alert Upon Detection for CVE-2022-30190
On May 27, 2022, an interesting Microsoft Word doc was uploaded to VirusTotal by an independent security research team called nao_sec. The Word doc contains built-in code that calls an HTML file from a remote source that in-turn executes more (malicious) code and Microsoft Defender for Endpoint misses detection. Two days later, May 29, Kevin Beaumont publishes an article describing the behavior of this Word doc, and deems this a new 0-day vulnerability in Office/Windows products.