Operations | Monitoring | ITSM | DevOps | Cloud
Windows
Monitor Windows Performance Counters with Datadog
The Ultimate Guide to Windows Event Logging
4 Ways to Easily Disable Windows Updates in Desktops and Servers
How to Enable and Disable Kernel-mode Hardware-enforced Stack Protection
As technology evolves, with hackers perpetually sharpening their tools to breach our digital walls, understanding your computer’s built-in defenses is crucial. Kernel-mode hardware-enforced stack protection is one such mechanism. This article will look into the intricacies of this feature, as well as how to enable and disable kernel-mode hardware-enforced stack protection.
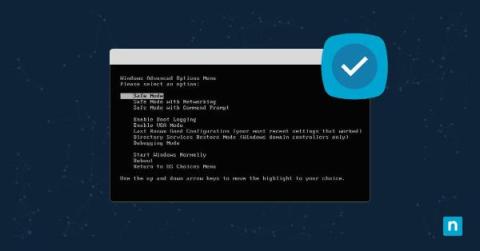
How to Start Safe Mode with Windows Command Prompt
Your computer has just decided to throw a digital tantrum, and all the regular troubleshooting tricks just aren’t cutting it. You know that there’s something awry under the hood of your Windows operating system, but navigating the litany of errors is making your head spin. Fortunately, there’s another option: entering Safe Mode via Windows Command Prompt.
3 Ways to Boot Windows in Safe Mode with Networking
We all know the situation: You’re about to start working on your Windows machine, but instead of the familiar welcome chime and desktop, you’re greeted by relentless error messages, unpredictable system behavior, or even the infamous Blue Screen of Death. The good news is there’s a troubleshooter at your disposal. Safe Mode with Networking is the easiest way to troubleshoot issues and get back online quickly. So how can you boot Windows in Safe Mode with Networking?
How to Export a Windows Registry Key
Navigating the Windows system registry can seem like traversing a minefield, especially if you are new to it—a single misstep could create complex issues in your system. Specifically, incorrect manipulations of the registry key might lead to errors or even complete system crashes. Fortunately, understanding how to export a registry key can make things significantly easier and safer. Below, we’ll talk through some of the basics of Windows Registry operations.
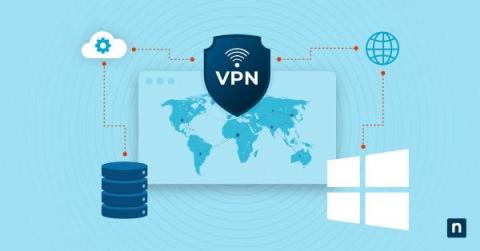
How to Install and Set up a VPN on Windows Server 2022
A VPN, or Virtual Private Network, enables secure communications over an untrusted network. It enables users to connect to servers and networks from virtually anywhere, creating a secure tunnel between the user and a remote network or server. VPNs ensure data privacy and prevent unauthorized access, ensuring the data transmitted remains confidential and protected from external threats.
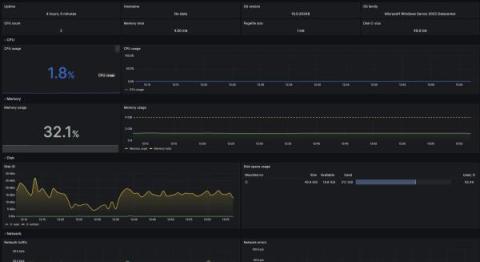
Monitoring Microsoft Windows with Grafana Cloud: new updates
Windows is widely used by developers, businesses, and individuals alike. Renowned for its adaptability, security, and reliability, the operating system is a preferred choice for servers, desktops, and embedded devices. It also holds a significant presence in the cloud, serving as the foundation for numerous major websites and applications.