Operations | Monitoring | ITSM | DevOps | Cloud
Latest News
Google's New 'Badge of Shame' for Slow Websites
Google recently announced a new ‘Badge of Shame’ for slow websites in Chrome to improve user experience. We explain what this new badge means for websites and provide some tips to help you speed up your site.
Plugging Git Leaks: Preventing and Fixing Information Exposure in Repositories
Have you ever been neck-deep building a new feature? You're working at capacity. You need to test something out so you paste an API key into your source file with every intention of removing it later. But you forget. You push to GitHub. It's an easy mistake, and potentially a very expensive one. In this article, Julien Cretel explores the nuances of this kind of data leak, offers suggestions for recovery when leaks happen and gives us options for preventing them in the first place.
A PagerDuty Security Debrief
Today is day one of the RSA Security Conference in San Francisco, where thousands of security professionals from around the world come together to share new ideas, discuss global security vulnerabilities, and explore the latest technologies in the security industry.
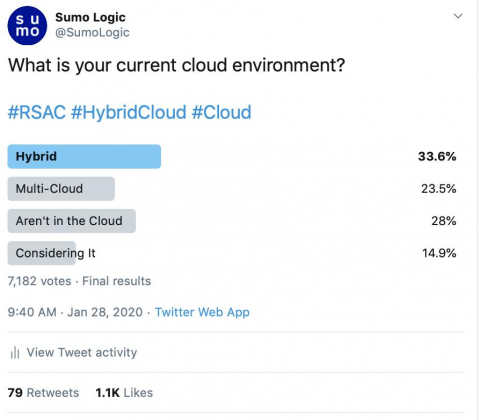
Pre-RSA Twitter Poll: 3 Interesting Observations on SOC, SIEM and Cloud
The Power of Splunk Security Essentials + Accedian Skylight Powered Security
As new technologies emerge, end-to-end application stacks continue to grow, and connected devices become more omnipresent in everyday lives, our society will only become more intrinsically connected across multiple touchpoints. It’s even estimated that in the US alone, there will be roughly 200 billion IoT devices by the end of 2020.
Image scanning for CircleCI
In this blog post, we are going to cover how to perform container image scanning for CircleCI using Sysdig Secure. Image scanning allows DevOps teams to detect and resolve issues, like known vulnerabilities and incorrect configurations, directly in their CI/CD pipelines. Using Sysdig Secure, you can enforce image policies to block vulnerabilities before they reach production environments and fix them faster while the developer still has the context.
SIEM Yara Rules
Mac system extensions for threat detection: Part 3
This is the third and final post of a three-part series on understanding kernel extension frameworks for Mac systems. In part 1, we reviewed the existing kernel extension frameworks and the information that these frameworks can provide. In part 2 we covered techniques that could be used in kernel to gather even more details on system events. In this post, we will go into the new EndpointSecurity and SystemExtensions frameworks.
Introducing the Splunk for CMMC Solution
On January 31st, 2020, the Office of the Undersecretary of Defense for Acquisition and Sustainment (OUSD A&S) published V1.0 of the Cybersecurity Maturity Model Certification (CMMC). The CMMC builds on DFARS both in terms of required practices and by establishing “trust, but verify” relationships with DoD contractors.