Operations | Monitoring | ITSM | DevOps | Cloud
Compliance
Blancco's Data Erasure Solutions Empower DoD Contractor Compliance with CMMC 2.0 Media Protection Requirement
IT Ops' role in strengthening security and achieving compliance
It wouldn’t be Cybersecurity Awareness month without some spooky-themed blogs with language focused on Fear, Uncertainty, and Doubt (FUD). Luckily, it’s the end of November now, and this isn’t that kind of blog, but what was true in October is still true today. I won’t tell you that you need to be afraid of bad actors infiltrating your security defenses and wreaking havoc in your infrastructure. Why? Because you are likely stressed enough already. Don’t you think?
How Automation Takes the Time and Guesswork Out of Security Compliance
Episode 1: DevSecOps Coffee Break Series Add OSS Security & Compliance to Artifactory
Obfuscate user data with Session Replay default privacy settings
Session Replay enables you to replay in a video-like format how users interact with your website to help you understand behavioral patterns and save time troubleshooting. Visibility into user sessions, however, can risk exposing sensitive data and raise privacy concerns. For example, a user session may include typing in a credit card or social security number into an input field.
Deploy Friday: E79 The Long and Winding Road towards security compliance
ServiceNow Privacy Management Overview
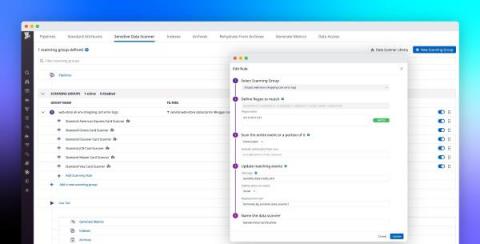
Build a modern data compliance strategy with Datadog's Sensitive Data Scanner
Within distributed applications, data moves across many loosely connected endpoints, microservices, and teams, making it difficult to know when services are storing—or inadvertently leaking—sensitive data. This is especially true for governance, risk management, and compliance (GRC) or other security teams working for enterprises in highly regulated industries, such as healthcare, banking, insurance, and financial services.
Who needs CMMC certification (Resource Guide for 2022)
If your company works with the US Department of Defense (DoD) as a contractor or subcontractor, you will need to prepare to meet CMMC requirements in order to successfully bid on and win contracts. This recent development has been a significant adjustment for small organisations who wish to work with or continue working with the DoD.